The Ultimate Guide to Unlocking the Hidden Privacy Gems of iCloud

Discover the essential iCloud privacy features! Safeguard your personal data with App Tracking Transparency, iCloud Private Relay, Mail Privacy Protection, Hide Your Email, Password Leak Scanner, and secure your information with iCloud
In today's digital world, where online privacy is constantly under threat, Apple's iCloud offers innovative solutions to keep you and your data secure. Recognizing the value of information in today's society, tech companies are continuously seeking ways to gather as much data as they can. However, Apple stands apart by prioritizing privacy and has incorporated various features within iCloud to cater to privacy-conscious users.
If you're already spending money on an iCloud+ subscription, here's how you can better protect yourself online:
App Tracking Transparency (ATT)
Developers sometimes add unnecessary permissions that enable them to access extra data from your device through other apps and websites. This deceptive tactic is often employed to gather data that can be sold to the highest bidder, even though the data is not required for the app's intended purpose.
Fortunately, Apple introduced the App Tracking Transparency (ATT) feature in 2021. This feature empowers you to have greater control over your data by allowing you to manage how app developers track and collect it.
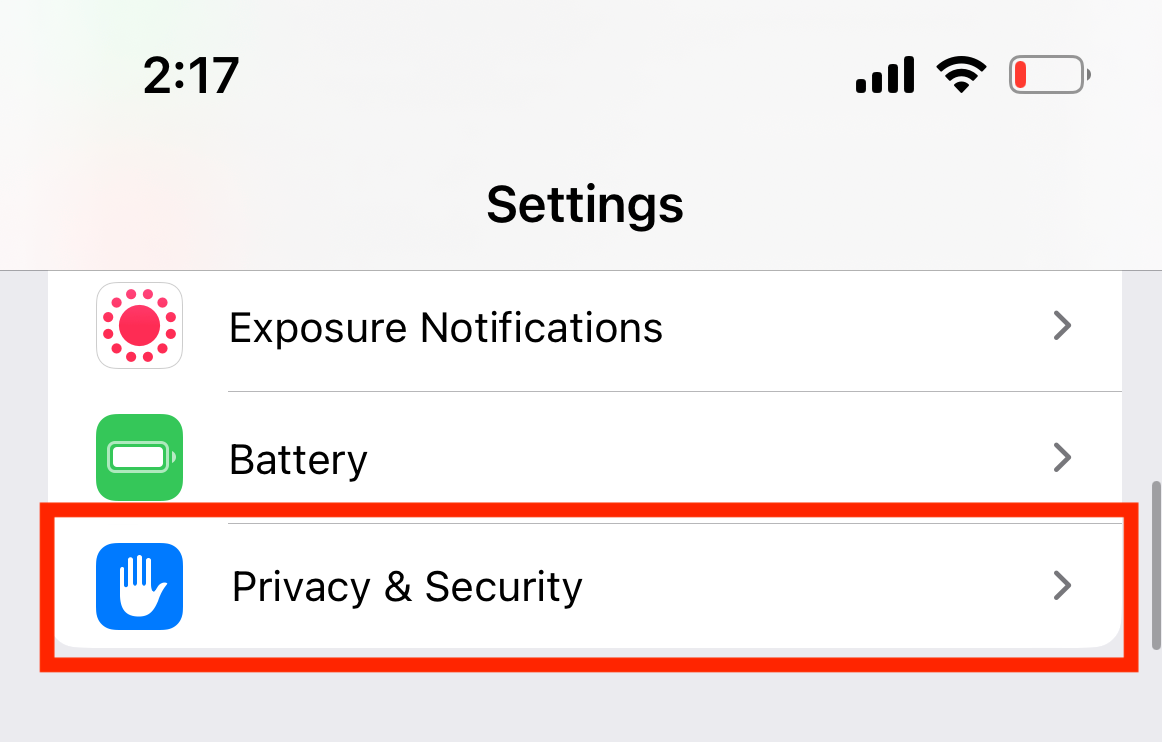
To automatically deny all app tracking requests from new apps, open the Settings app on your iPhone and tap Privacy & Security.
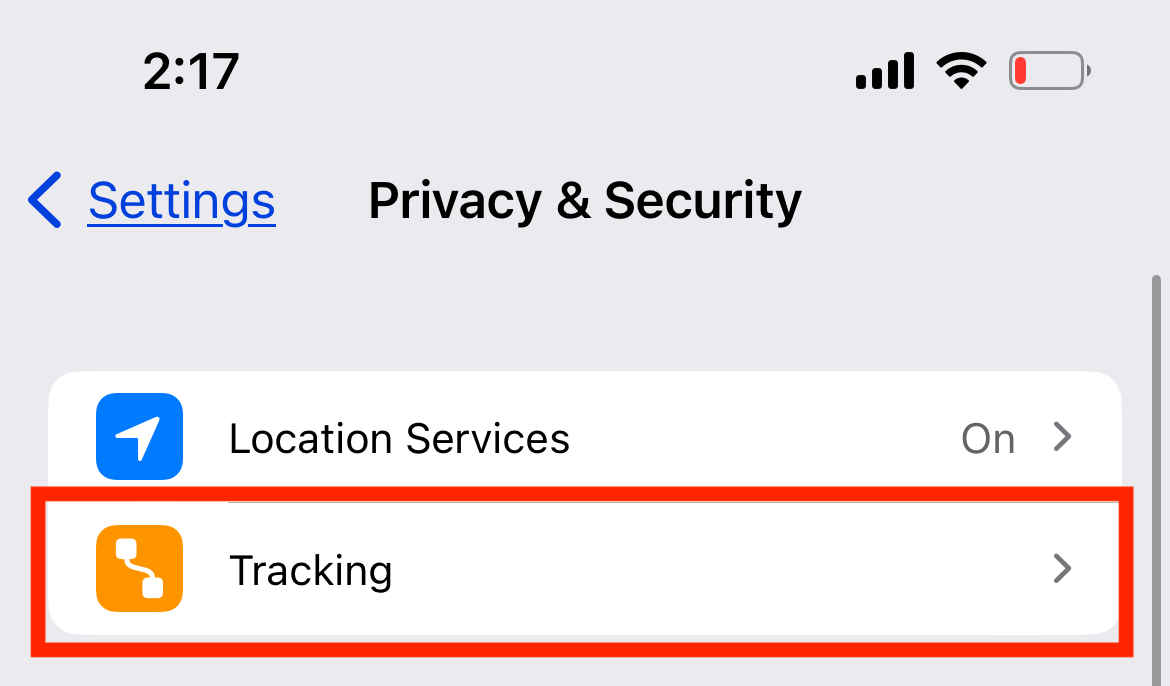
Next, in the upper portion of the screen, tap Tracking.
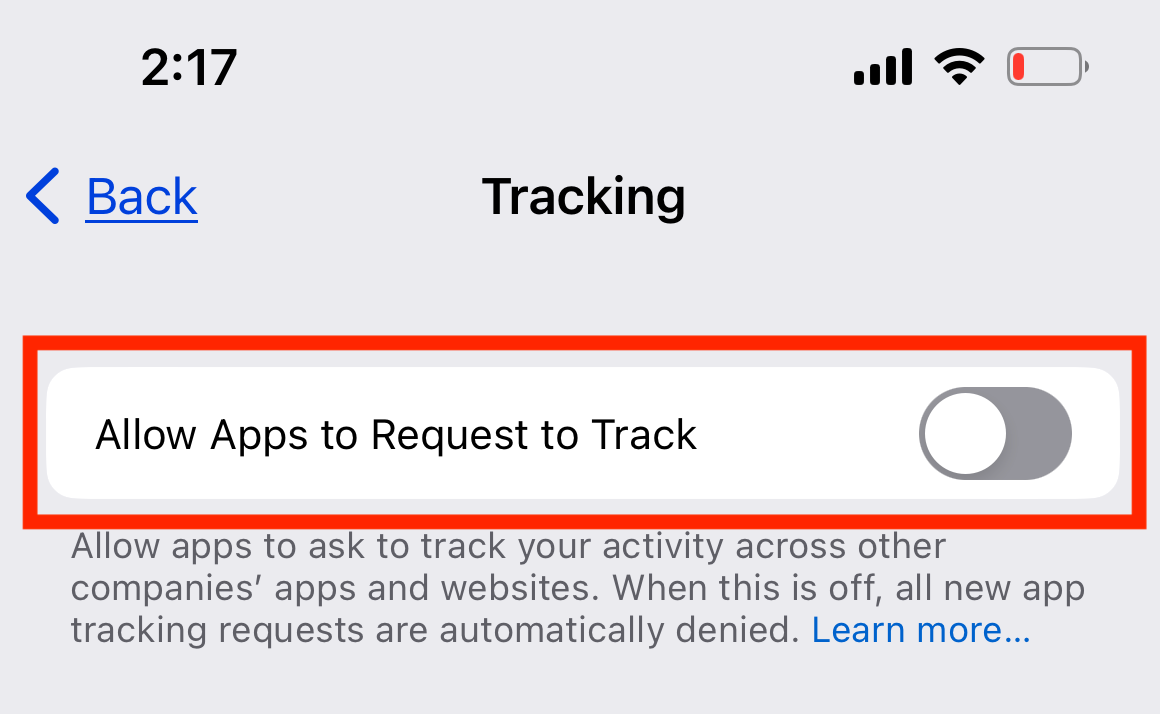
Lastly, next to Allow Apps to Request to Track, toggle off the button.
Afterwards, any new applications that desire to monitor your activity on other applications will be required to obtain your consent through a pop-up notification. Within the notification, you have the choice to either select "Decline app tracking" or "Authorize." Generally, when it involves sharing your data unnecessarily, it is always advisable to opt for refusing.
iCloud Private Relay
Centralizing data enhances its ability to anticipate your purchasing patterns or propensity to make decisions based on past data. This makes centralized data highly appealing to individuals seeking to profit from it. Although there are advantages to this, like receiving improved recommendations on shopping apps and relevant ads, having a detailed customer profile poses its own risks.
Fortunately, for iCloud+ subscribers, Apple has introduced iCloud Private Relay as a solution to decentralize your browsing activity gradually.
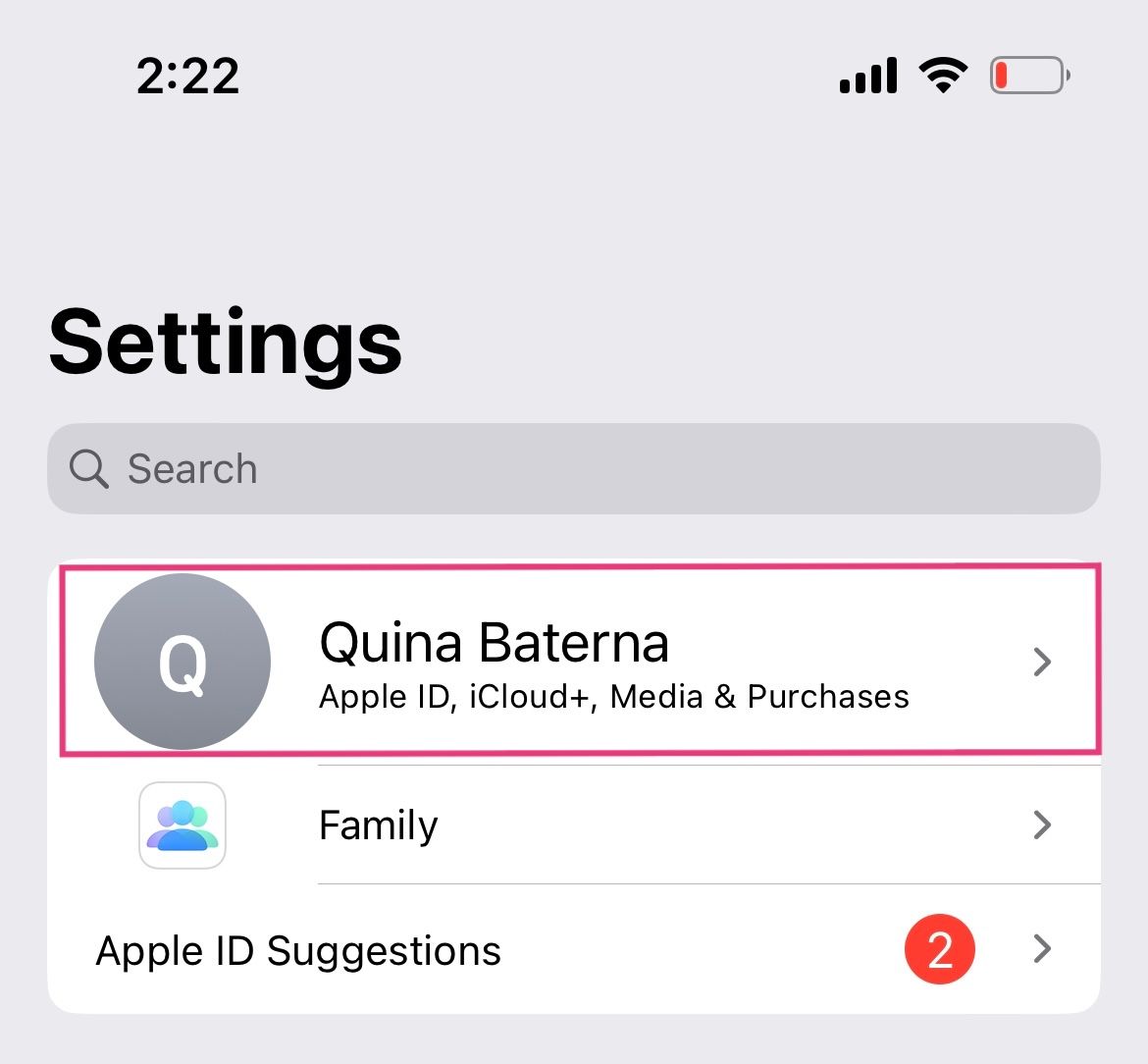
To activate iCloud Private Relay on your iPhone, open the Settings app and select your Apple ID name.
In the Apple ID page, select "iCloud."
Under iCloud+, tap "Private Relay." In the event that Private Relay is not available in your country, there will be "Not Supported" written next to the arrow.
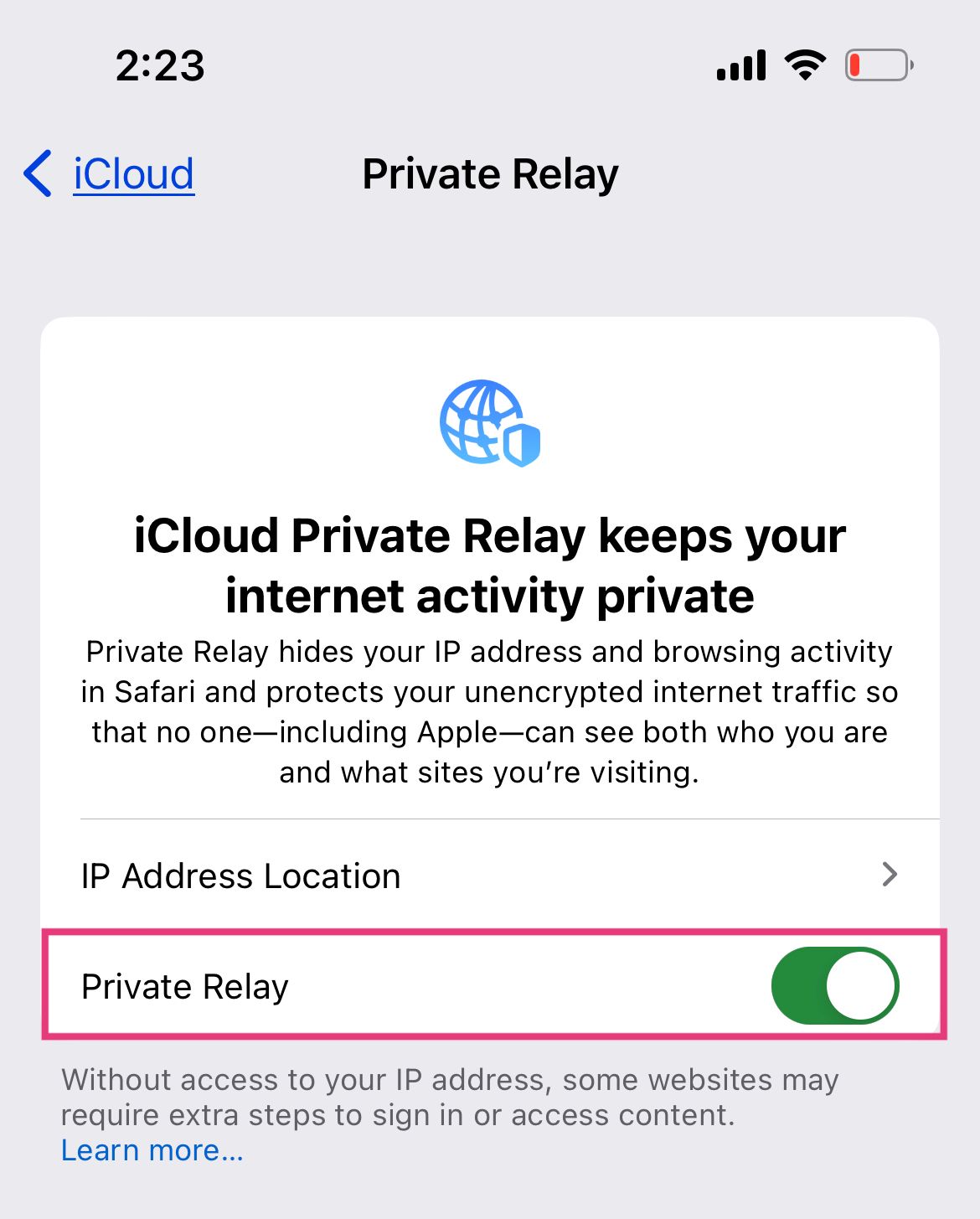
To seal the deal, next to Allow Apps to Request to Track, toggle on the button.
Encrypting DNS traffic is crucial as it safeguards your browsing history from potential threats like internet service providers and hackers accessing your local Wi-Fi network. Furthermore, it provides protection against DNS hijacking, where malicious individuals attempt to mimic legitimate websites like your bank, aiming to pilfer your login credentials.
Mail Privacy Protection
According to Apple, Mail Privacy Protection offers a safeguard that blocks senders from detecting the opening of their emails and from accessing your IP address when loading the email's content. Hence, if you desire to read emails without alerting the sender, this could prove to be a useful solution.
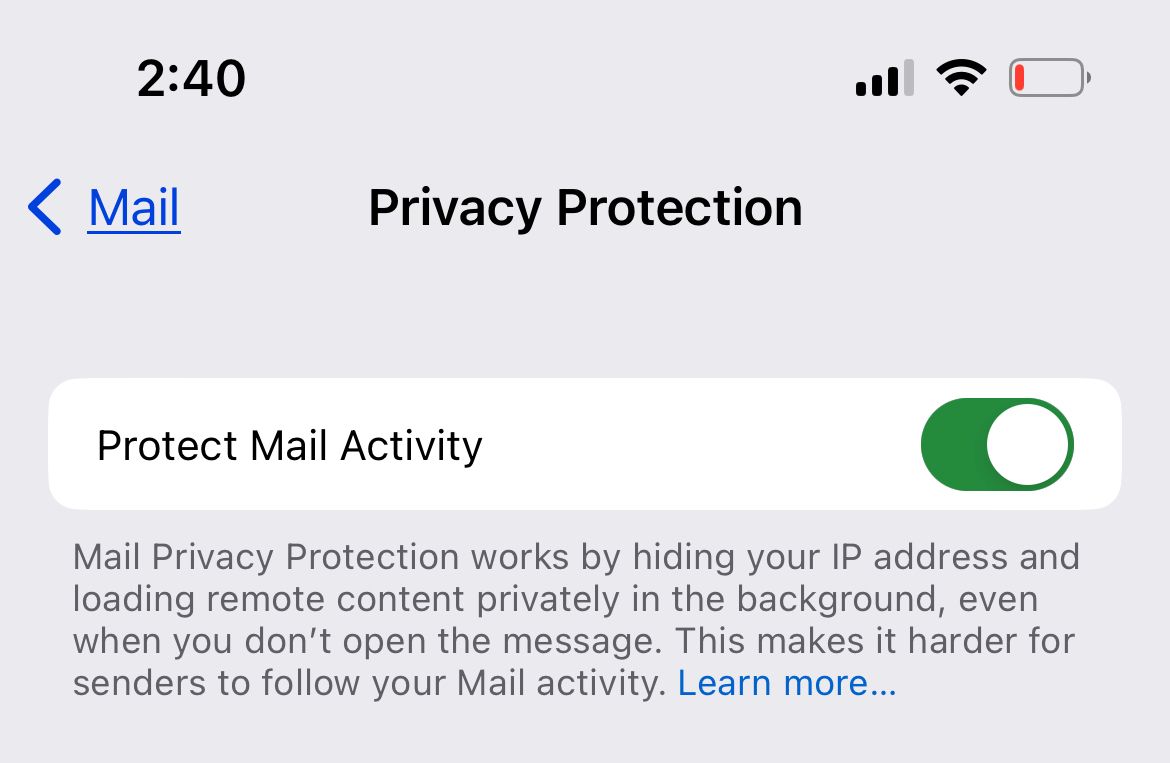
To enable Mail Privacy Protection on your iPhone, open the Settings app and tap "Mail."
Under Messages, select "Privacy Protection."
Next to Protect Mail Activity, toggle on the button.
Once you activate this feature, you will be able to send and receive emails through the Apple Mail app as usual, but with enhanced security measures. It is vital to note that the Mail Privacy Protection feature solely functions with emails sent to your Mail app. Therefore, if you are currently using a different app to access your emails, it might be worth giving Apple Mail another chance.
Hide Your Email
To send an email using an Apple-generated email address on your iPhone, simply follow these steps:
1. Open your Mail app on your iPhone or iPad.
2. Locate the New Message icon displayed in the lower-right corner of the screen.
3. Tap on the New Message icon to begin composing a new email.
Next, fill out the rest of the email, such as the recipient, subject, and body. Then, tap "From." Select "Hide My Email" in the drop-down screen.
When leveraging the Hide Your Email functionality on iCloud, you are restricted to the option of sending an email to just a single recipient in one go. Subsequently, upon receiving a response from this recipient, their email will be automatically forwarded to your inbox. From there onward, you can carry on the conversation utilizing your actual email address, whereas the recipient will still only be able to perceive your randomized email address.
Password Leak Scanner
Keeping track of all the accounts created over the course of one's internet history can be a daunting task for the average person. In fact, it is not uncommon for individuals to struggle with remembering the numerous accounts they have had to create in order to access various online services, let alone recall the passwords associated with each one.
To enhance the security of your life, it is crucial to avoid poor password practices. Cyber criminals are always ready to exploit your identity or gain unauthorized access to your online banking details. Luckily, Apple offers a solution by allowing you to verify if your passwords have been compromised on the dark web or any other well-known online platforms.
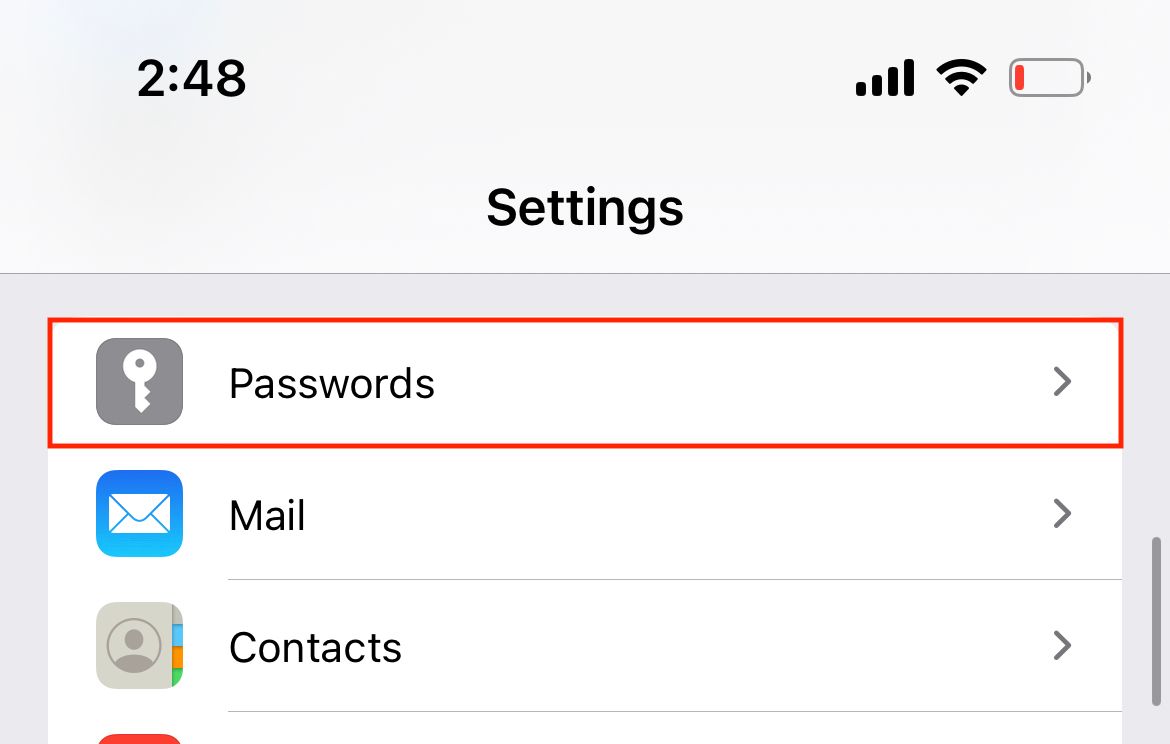
To activate the feature of detecting compromised passwords for your iCloud-connected accounts, simply navigate to the Settings application and choose the "Passwords" option.
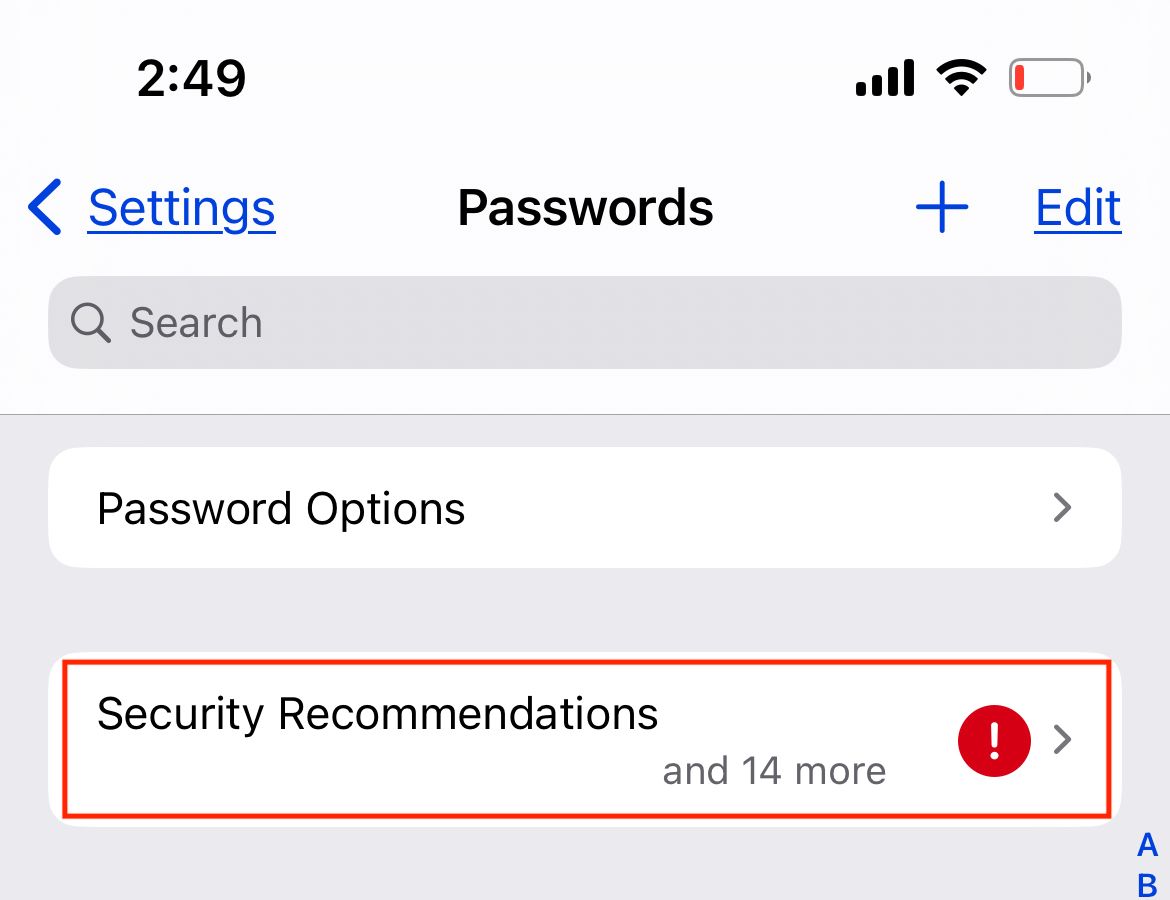
In the upper portion of the screen, tap "Security Recommendations."
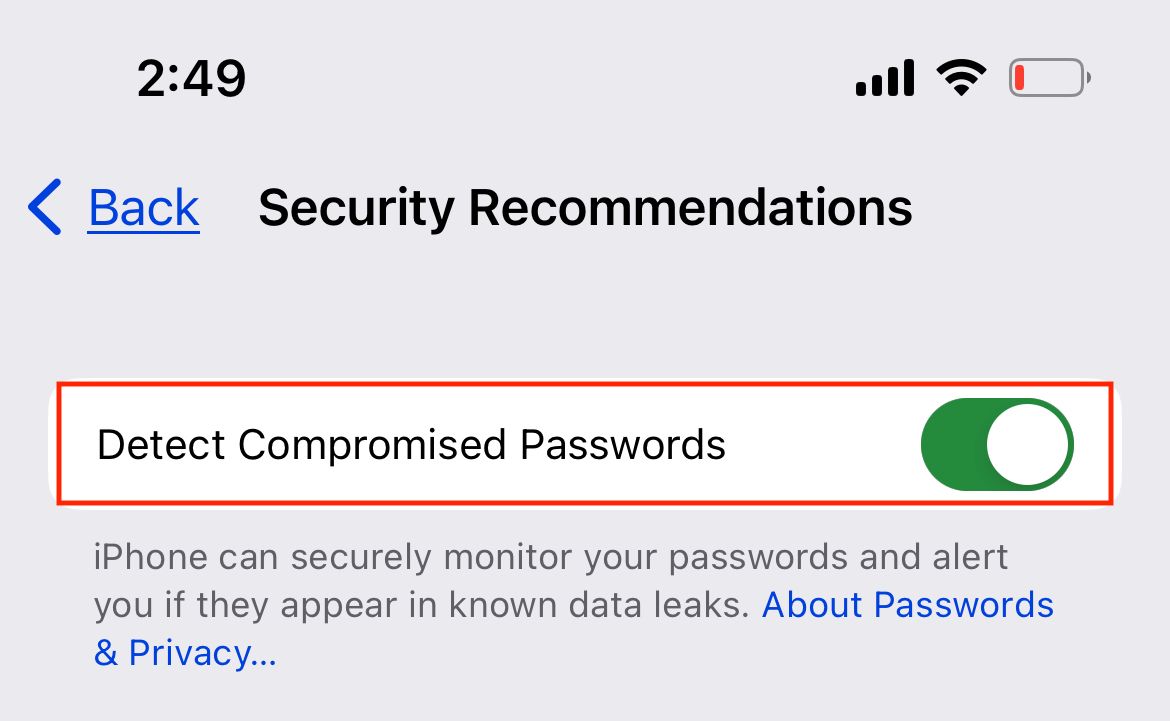
Then, next to Detect Compromised Passwords and toggle on the button.
Once activated, you will have continual access to these suggestions. In addition to detecting passwords compromised in data breaches, this iCloud function will alert you if your password is susceptible to guessing and advise against reusing passwords.
Keep Your Data Safe with iCloud
Having these iCloud features at your disposal undoubtedly puts you in a stronger position compared to not having them. However, it is important to remember that simply being aware of these features is just the first step. Without exercising caution, many of these features can have both positive and negative consequences. Take, for instance, the App Privacy Report, which tracks your phone's activities but also poses a potential privacy risk.
Furthermore, it is crucial to grasp the difference between security and privacy. Although these iCloud features may provide a certain level of privacy and allow you to control who can access your information, it is necessary to implement extra measures to ensure complete security. This includes creating stronger passwords, utilizing OTPs for log-ins, and exercising caution when installing apps on your devices to prevent any potential leaks from causing harm.