Secure Your Linux System: Disabling Root Login over SSH—The How and Why

Enhance security with this guide on disabling root login over SSH in Linux Protect your system from unauthorized access and ensure a safer environment
Key Takeaways
Accessing the Linux root user poses significant risks due to its possession of all-encompassing privileges. Moreover, logging in as root through SSH exacerbates the situation by creating a possibility for remote attackers to gain unauthorized entry to your system.
Linux distributions often discourage logging in as a root user and instead advocate for utilizing the sudo command to temporarily elevate privileges when necessary. This approach helps mitigate the potential for errors or malicious activities.
When enabling root access through SSH, it is more secure to employ SSH keys rather than passwords. This precautionary measure eliminates the risk of brute-force attacks and unauthorized entry.
It is not recommended to log in as the Linux root user. Logging in as root through an SSH connection is even more discouraged. In this article for Cybersecurity Awareness Week, we explain the reasons behind this and provide preventive measures. This piece of content is presented in collaboration with Incogni.
What is root on Linux?
To effectively manage and control critical and sensitive components of your operating system, you require the expertise of an individual possessing the necessary authority. This is where root comes into play. In Unix and Linux operating systems, root assumes the role of an omnipotent superuser.
The root user account is safeguarded by a password, just like any other account. Without knowing the root user's password, no one else can gain access to that account. Consequently, the privileges and powers granted to the root user cannot be exploited by anyone else. On the other hand, the only barrier preventing a malicious user from utilizing root's powers is the password itself. Unfortunately, passwords can be easily guessed, deduced, discovered written down somewhere, or forcefully cracked.
In the event that a malicious attacker obtains root's password, they can log in and exercise unrestricted control over the entire system. With root's elevated privileges, there are no limitations on their actions. It would be as if the root user had simply walked away from a terminal without logging out, thereby enabling opportunistic access to their account.
Due to these risks, most contemporary Linux distributions no longer permit local or SSH login for the root user. Although the root user still exists, no password is assigned to it. However, system administration tasks still need to be performed. To address this dilemma, the sudo command is employed.
Sudo enables authorized users to temporarily utilize root-level privileges while remaining within their own user accounts. To authenticate and use sudo, you must enter your own password. This grants you temporary access to the capabilities of the root user.
Closing the terminal window in which your root powers were utilized results in the termination of those powers. However, leaving the terminal window open will lead to an automatic timeout, subsequently returning you to your regular user status. This feature serves as an additional protective measure, safeguarding you from potential harm caused by your own actions. Opting to consistently log in as root rather than using a regular account increases the risk of catastrophic errors on the command line. Conversely, utilizing sudo for administrative tasks encourages a heightened sense of focus and caution in your typing.
Allowing root login over SSH increases the risks because attackers don't have to be local; they can try to brute-force your system remotely.
The root User and SSH Access
When administering systems for others, you may encounter this issue more frequently. In some cases, individuals set a root password to enable login access. However, additional settings must be modified to permit root login via SSH.
These actions are usually intentional and not accidental. However, they may be performed by individuals who are unaware of the potential risks involved. If you assume responsibility for a computer that is configured in this manner, it is essential to explain to the owners the drawbacks of this setup and restore the system to a secure state. The owners may not be aware if it was configured by the previous system administrator.
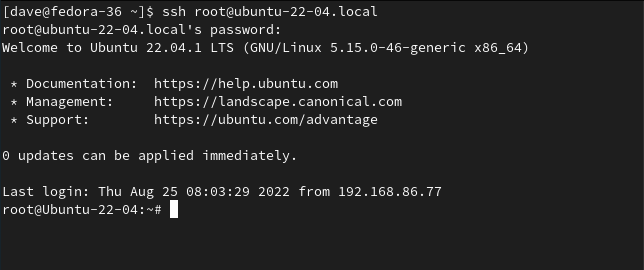
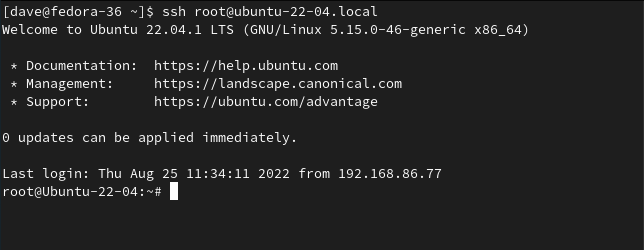
Here's a user on a computer running Fedora, making an SSH connection to an Ubuntu computer as the root user of the Ubuntu computer.
ssh root@ubuntu-22-04.local
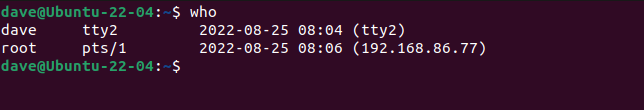
The Ubuntu computer allows the root user to log in over SSH. On the Ubuntu computer, we can see that a live connection is underway from the root user.
who
Disabling SSH Access for root
Unknown is the identity of the user utilizing the session. It remains uncertain whether the individual on the receiving end of the SSH connection holds the status of a root user or has somehow acquired root's password.
To disable SSH access for the root user, the SSH configuration file located at "/etc/ssh/sshd_config" must be modified using sudo.
sudo nano /etc/ssh/sshd_config
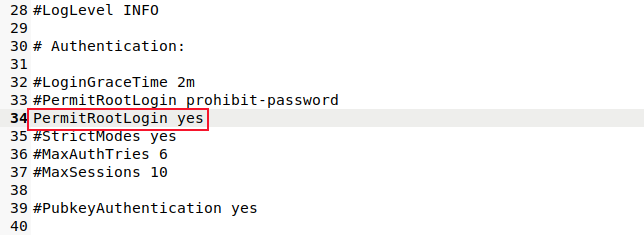
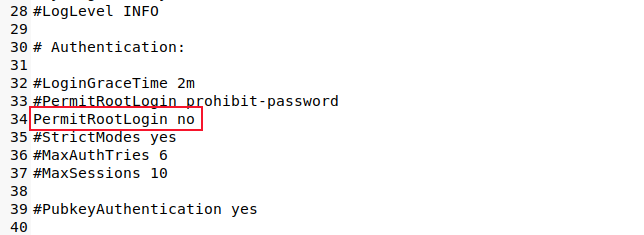
Scroll through the file or search for the string "PermitRootLogin."
Either set this to "no" or comment the line out by placing a hash "#" as the first character on the line. Save your changes.
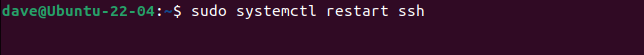
We need to restart the SSH daemon so that our changes come into effect.
sudo systemctl restart ssh
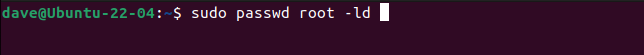
If you also want to prevent local logins, disable root's password. We're taking a belt and braces approach and using both the -l (lock) and -d (delete password) options.
sudo passwd root -ld
This locks the account and removes the account password into the bargain. Even if the root user is physically sitting at your computer they won't be able to log in.
A Safer Way to Allow root SSH Access
In certain cases, there may be reluctance from managers to eliminate root access via SSH. In the event that they remain adamant, you might find yourself compelled to restore it. In such a scenario, it is important to seek a compromise that minimizes risk while still allowing remote logins from the root user.
Utilizing SSH keys for SSH connections provides significantly enhanced security compared to using passwords. Since passwords are not utilized in this process, they are immune to brute-force attacks, guessing, or any other form of discovery.
Prior to securing the local root account, establish SSH keys on the remote computer to enable the root user's connection to your local computer. Subsequently, proceed with erasing their password and locking their local account.
We'll also need to edit the "sshd_config" file once more.
sudo gedit /etc/ssh/sshd_config
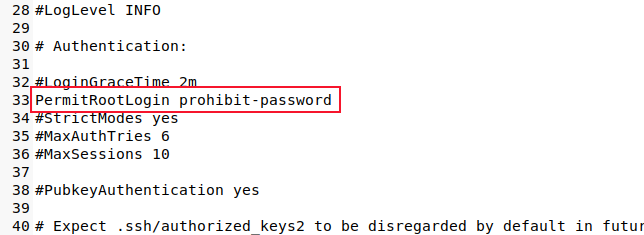
Change the "PermitRootLogin" line so that it uses the "prohibit-password" option.
Save your changes and restart the SSH daemon.
sudo systemctl restart ssh
Now, even if the root user's password is restored, it will not grant access to log in via SSH using a password.
When the remote root user establishes an SSH connection to your local computer, the keys are exchanged and verified. If the authentication is successful, the root user is connected to your local computer without requiring a password.
ssh root@ubuntu-22-04.local
No Entry
Refusing remote connections from the root user is the best option. Allowing root to connect using SSH keys is second best, but still a lot better than using passwords.