Mastering Reverse SSH Tunneling: A Step-by-Step Guide to Effortlessly Harness Its Power

Unlock the potential of reverse SSH tunneling to reach inaccessible Linux computers Discover the mechanics behind this powerful tool and master its usage effortlessly
Key Takeaways
Use reverse SSH tunneling when you need to connect to a remote computer that is hard to reach due to firewall rules or complex network configurations.
Reverse SSH tunneling enables you to establish a new connection from your local computer to the remote computer by utilizing the current connection.
To enhance convenience and eliminate password challenges, configure SSH keys to facilitate the connection from the remote computer to the local computer.
Need to SSH to an unreachable Linux computer? Have it call you, then burrow down that connection to get your own remote SSH session. We show you how.
When You'll Want to Use Reverse SSH Tunneling
Remote computers can sometimes be difficult to access due to strict firewall rules at their location or complex Network Address Translation rules set up by the local admin. So, how can you establish a connection with such a computer? To establish clarity, let's assign labels: your computer will be referred to as the local computer since it is in close proximity to you, while the computer you intend to connect to will be referred to as the remote computer because it is located elsewhere.
In order to distinguish between the local and remote computers mentioned in this article, the remote computer is referred to as "howtogeek" and is operating on Ubuntu Linux (displaying purple terminal windows). The local computer, on the other hand, is named "Sulaco" and is running Manjaro Linux (with yellow terminal windows).
Typically, one would establish an SSH connection from the local computer to connect with the remote computer. However, in the networking scenario described here, this option is not feasible. Regardless of the specific network issue at hand, this method proves beneficial whenever direct SSH access to a remote computer is unavailable.
If your networking configuration is simple, the remote computer can establish a connection with you. However, this connection alone is not enough to fulfill your requirements as it doesn't allow for a functional command-line session on the remote computer. Nevertheless, it serves as a starting point, establishing a connection between the two computers.
The solution lies in utilizing reverse SSH tunneling.
What Is Reverse SSH Tunneling?
Reverse SSH tunneling allows you to use that established connection to set up a new connection from your local computer back to the remote computer.
Using the original remote computer connection to travel in the opposite direction is known as "reverse" usage. Since SSH is secure, this entails encapsulating a secure connection within another secure connection. Consequently, your connection to the remote computer functions as a private tunnel within the original connection. Hence, the term "reverse SSH tunneling" is derived.
How Does SSH Reverse Tunneling Work?
Reverse SSH tunneling relies on the remote computer using the established connection to listen for new connection requests from the local computer.
The remote computer establishes a network connection with the local computer by listening on a designated port. When an SSH request is detected on that port, the remote computer redirects the connection request back to itself, effectively creating a new connection from the local computer to the remote computer. Setting up this process is simpler than explaining it.
Using SSH Reverse Tunneling
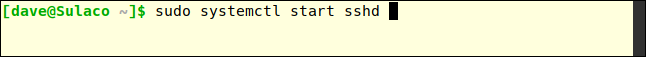
SSH will already be installed on your Linux computer, but you may need to start the SSH daemon (sshd) if the local computer has never accepted SSH connections before.
sudo systemctl start sshd
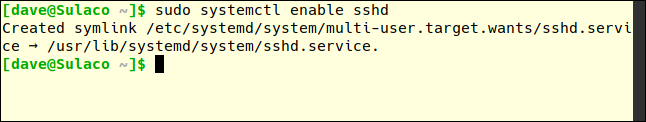
To have the SSH daemon start each time you reboot your computer, use this command:
sudo systemctl enable sshd
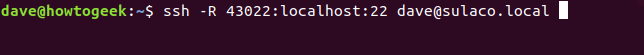
On the remote computer, we use the following command.
The -R option in ssh instructs to establish new SSH sessions on the remote computer.
The "43022:localhost:22" specifies that connection requests to port 43022 on the local computer should be redirected to port 22 on the remote computer. Port 43022 is selected as it is listed as unallocated and does not hold any special significance.
dave@sulaco.local is the user account the remote computer is going to connect to on the local computer.
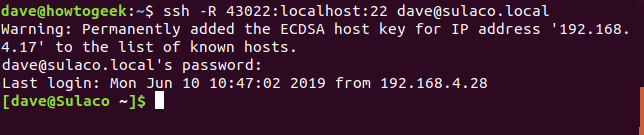
ssh -R 43022:localhost:22 dave@sulaco.local
When you attempt to connect to the local computer for the first time, you may receive a warning message. Alternatively, if the connection details are being added to the list of recognized SSH hosts, a warning might also appear. The warning message, if any, varies depending on whether previous connections have been established from the remote computer to the local computer.
You will be prompted for the password of the account you are using to connect to the local computer.
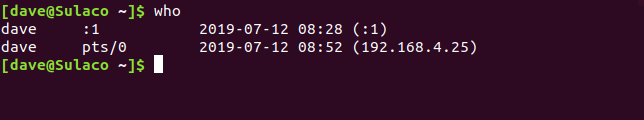
After establishing the connection, the command prompt transitions from dave@howtogeek to dave@sulaco. As a result, we are now connected to the local computer remotely. This allows us to execute commands on it. To view the logins on the local computer, we can utilize the who command.
who
Connecting to the Remote Computer
It is evident that the individual identified as dave has successfully accessed the local computer with their user account. Additionally, the remote computer has established a connection, utilizing the same user credentials, from the IP address 192.168.4.25.
Since the remote computer is successfully connected and actively listening for connections, we can proceed with attempting to connect to it from the local computer.
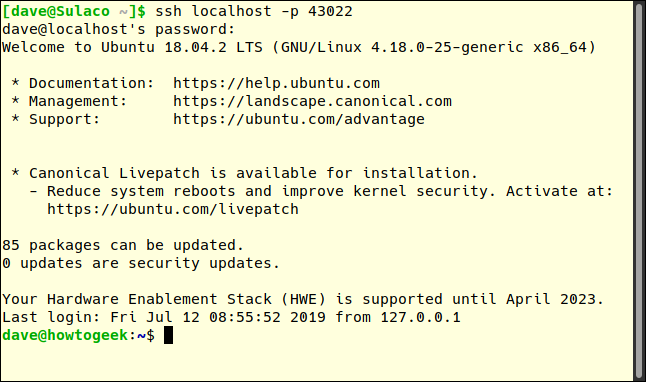
To establish a connection to the remote computer, we need to instruct ssh to connect to the local computer on port 43022, which may seem counter-intuitive. However, this connection request will then be forwarded to the remote computer.
ssh localhost -p 43022
We are asked to enter the user account password and then establish a connection to the remote computer from our local computer. Once connected, our Manjaro computer greets us with the message, "Welcome to Ubuntu 18.04.2 LTS".
Note that the command prompt has changed from dave@sulaco to dave@howtogeek. We've achieved our goal of making an SSH connection to our hard-to-reach remote computer.
Using SSH With Keys
To make it more convenient to connect from the remote computer to the local computer, we can set up SSH keys.
On the remote computer, type this command:
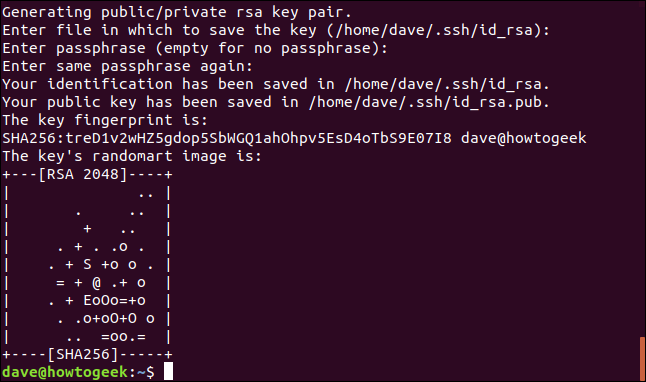
ssh-keygen
You will be asked for a passphrase. Pressing Enter to skip the passphrase questions is not advisable. This would allow anyone on the remote computer to establish an SSH connection to your local computer without being prompted for a password.
A strong passphrase can be created using three or four words separated by symbols.
Your SSH keys will be generated.
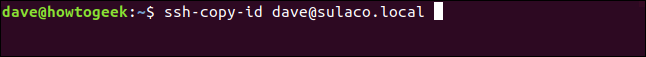
We need to transfer the public key to the local computer. Use this command:
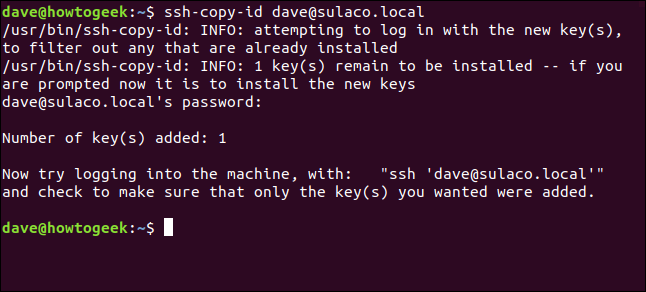
ssh-copy-id dave@sulaco.local
You will be prompted for the password for the user account you are logging in to, in this case, dave@sulaco.local.
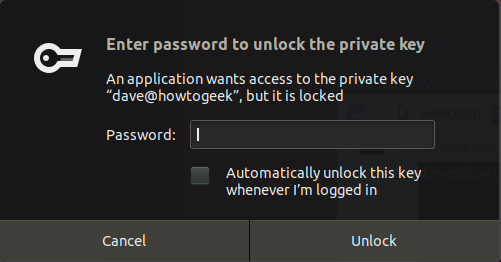
Upon your initial connection request from the remote computer to the local computer, you will be prompted to enter a passphrase. However, subsequent connection requests will not necessitate entering the passphrase, as long as the terminal window remains open.
Not All Tunnels Are Scary
Navigating through dark and twisty tunnels may seem challenging, but the process of reverse SSH tunneling becomes much simpler once you grasp the concept of maintaining a clear understanding between the remote and local computers. It's just a matter of reversing your perspective. To enhance convenience, consider setting up an SSH config file which enables streamlined functionalities such as tunneling or SSH agent forwarding.