Critical Vulnerability in Better Search Replace WordPress Plugin

A critical vulnerability in the Better Search Replace WordPress plugin was discovered and promptly patched by WP Engine. This vulnerability posed a serious threat to over 1 million active website installs and could lead to sensitive file retrieval and arbitrary code execution. Here's what you need to know about this critical security issue and how it was addressed.
Understanding the Severity of the Vulnerability
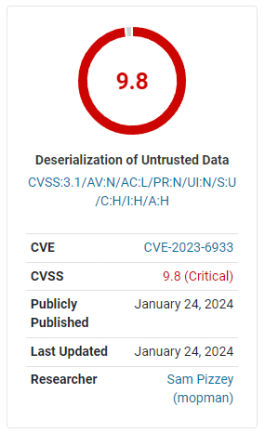
The severity of vulnerabilities in software systems is a critical aspect of cybersecurity. In the case of the Better Search Replace plugin for WordPress, a critical severity vulnerability with a score of 9.8 on the severity scale of 1-10 was identified. This means that the vulnerability was deemed the highest level of severity, posing a significant risk to website security.
Screenshot of severity score rating of 9.8 of a vulnerability discovered in Better Search Replace WordPress plugin
The severity of vulnerabilities is classified based on a point system, with ratings ranging from low to critical. A critical severity vulnerability is identified with a score within the range of 9.0-10.0. In this case, the critical severity of the vulnerability in the Better Search Replace plugin warranted immediate attention and action to mitigate potential security risks.
Insight into the Better Search Replace WordPress Plugin
The Better Search Replace plugin for WordPress, initially developed by the Delicious Brains development company and later acquired by WP Engine, is a widely used tool with over 1 million active installs. This plugin simplifies and automates the process of running a search and replace task on a WordPress website database, particularly useful in site or server migration tasks.
The plugin offers a range of features, including serialization support for all tables, the ability to select specific tables, and the option to run a 'dry run' to preview field updates. Additionally, it provides WordPress Multisite support and requires no server specifications beyond a running installation of WordPress.
The paid Pro version of the plugin includes advanced features such as change tracking, database backup and import capabilities, and extended support. The popularity of the Better Search Replace plugin stems from its user-friendly interface, practicality, and a reputation for reliability.
Understanding the PHP Object Injection Vulnerability
The critical vulnerability in the Better Search Replace plugin was attributed to a PHP Object Injection vulnerability, a serious application-level weakness that could lead to various malicious attacks, including code injection, SQL injection, and application denial of service. This vulnerability arises when user-supplied input is not securely unserialized, allowing attackers to inject arbitrary PHP objects into the application scope.
In the case of the Better Search Replace plugin, the vulnerability was exposed in the way it handled deserialization during search and replace operations. This vulnerability highlighted the lack of a POP chain, a series of linked classes and functions that attackers can exploit to trigger malicious actions when an object is unserialized. While the plugin did not contain such a chain, the risk remained if another plugin or theme installed on the same website contained a POP chain.