Boost Your Online Privacy with these Browser Extensions

Unveiling the Hidden Dangers: Browser Extensions pose a significant threat to your privacy, surpassing common perceptions Discover vital steps to minimize your risk
Browser extensions and add-ons have posed a substantial security threat for many years. One single malicious browser extension can easily expose your device details, browsing history, and other sensitive information to unauthorized entities. This risk is not hypothetical, but rather a continuous occurrence. This article for Cybersecurity Awareness Week is presented in collaboration with Incogni.
The Danger of Extensions
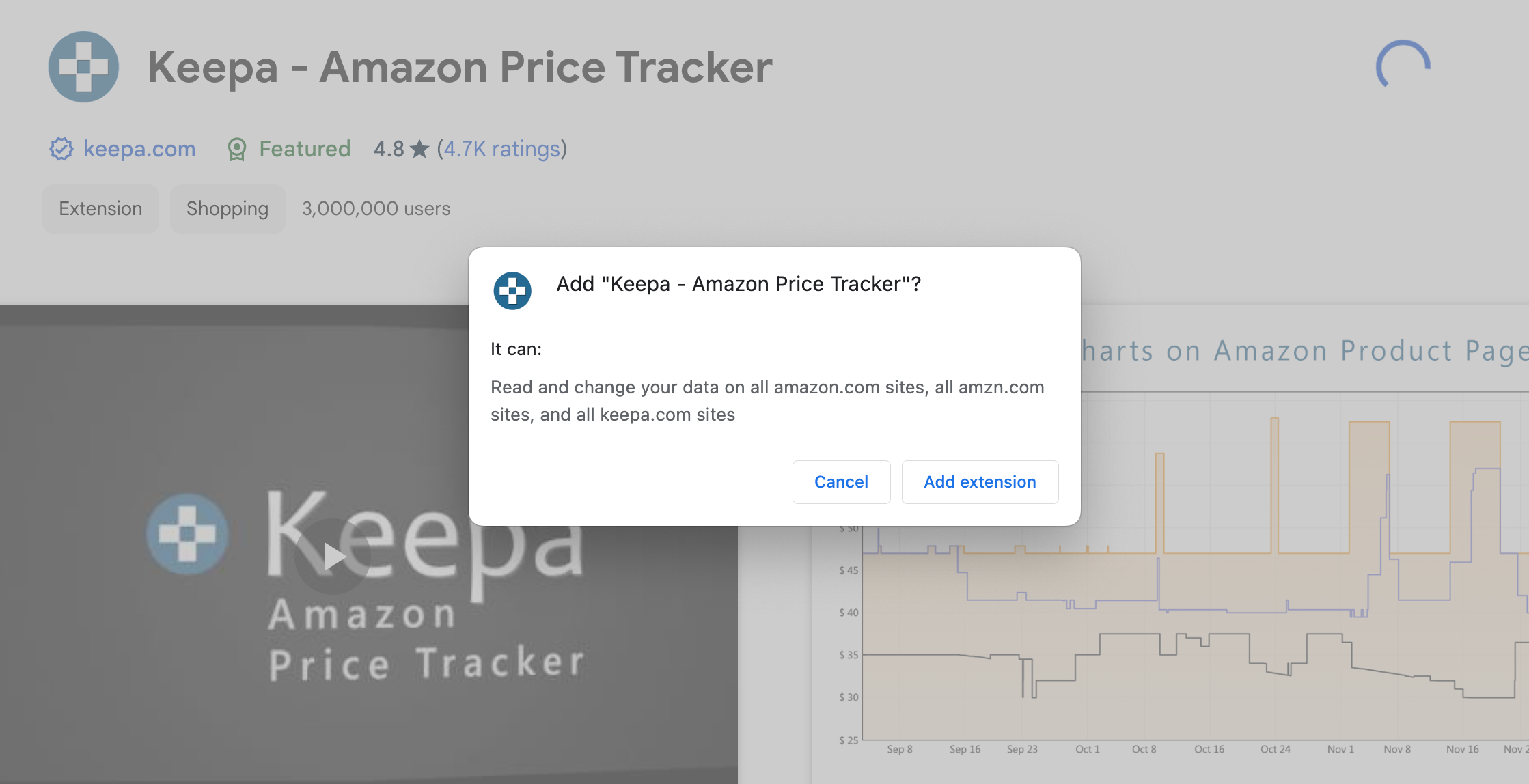
It is essential to review the browser extensions you have installed on your device as they have the ability to alter the content of web pages and even monitor the links you visit. This functionality requires extensive permissions that browsers are unable to adequately safeguard against in the event that an extension behaves maliciously. In such cases, the only recourse available to browsers is to ban these rogue extensions after they have already caused damage. Take the necessary steps to minimize the number of browser extensions installed on your system if you haven't done so already.Modern browser extensions, similar to Android and iPhone apps, operate based on a permissions model. They are designed to request only the necessary permissions for the promised features. Take the Keepa browser extension, for instance. It enhances Amazon product pages by providing price history graphs and additional buttons. To do this, it only seeks access to Amazon pages and its own website. Your data on YouTube, a bank website, Wikipedia, or any other platform would remain inaccessible.
However, several extensions are more generalized and require access to all the pages you visit. This includes writing and grammar assistants like Microsoft Editor and Grammarly that add text checking features to every supported page. While it is understandable, granting permission to access all the pages you visit is a significant level of trust. This is especially concerning considering that a large portion of our computer activity occurs within a web browser. It is similar to granting administrator permission to a Windows application.
To address these concerns, Google, Microsoft, and Mozilla have made efforts to manage extension permissions and offer less intimidating alternatives. For instance, some browser extensions can request permission only for the current tab rather than all websites indefinitely. Additionally, certain browsers restrict extensions from running on specific websites until explicitly allowed. However, there are limitations to the precautions that can be implemented if an extension requires access to everything and cannot function without it.
Avast and AVG's Online Security extensions in 2019 were discovered to be collecting and selling website visit data to various companies, including Home Depot, Google, and Pepsi, through Avast's subsidiary Jumpshot. Similarly, in 2016, the Web of Trust browser extension was found to be selling identifiable user data despite claiming it was anonymous. In 2018, Google removed four extensions with a combined download count exceeding 500,000, as they were secretly clicking on page ads without user knowledge. Another example is the Grammarly extension, which utilizes your writing to train AI models. These instances are just a few among many.
Furthermore, there have been cases of browser extensions being "hijacked" and transferred to different developers, allowing them to update the extension with malware. In 2017, the creator of the popular Web Developer for Chrome extension fell victim to a phishing attack on his Google account. The stolen account was then used to push an update injecting advertisements into web pages. Fortunately, the update was swiftly reversed. As a precautionary measure, Google now requires two-factor authentication for Google accounts with published extensions on the Chrome Web Store, aiming to reduce the risk of phishing and hacking attempts. Similarly, Mozilla has implemented a similar rule for developers who publish Firefox extensions.
Reduce Your Risk
To ensure your online safety, it is advisable to minimize the number of browser extensions you use. This precaution arises from the possibility that even seemingly safe extensions may unknowingly update with malicious software in the future. In order to review your list of extensions, access the chrome://extensions page on Google Chrome and Microsoft Edge. For Firefox users, either enter about:addons in the address bar or select "Add-ons and themes" from the main toolbar menu. Make sure to uninstall any unnecessary extensions.
If you occasionally require specific extensions while maintaining a high level of browsing security, you might consider utilizing a secondary browser exclusively for those extensions. Alternatively, some extensions offer alternative web applications with comparable functionality. As an illustration, instead of installing the Grammarly extension, which might collect your browsing data, you could employ their web app by copying and pasting text to examine spelling and grammar errors. Although this approach may be less convenient and time-consuming, it ensures enhanced security.