Beginner's Guide to Utilizing firewalld on Linux

Discover the ultimate guide to firewalld on Linux! Unleash the power of this user-friendly firewall as we explore installation, zones, service management, GUI usage, and more Don't miss out on this comprehensive resource!
Key Takeaways
Firewalld is a modern and powerful firewall for Linux that is easy to configure through the command line or GUI interface.
Firewalls play a crucial role in improving security by restricting and managing network connections to your computer.
Firewalld employs zones as a means of organizing firewall rules, enabling precise adjustment and customization to cater to varying security requirements.
Looking for a user-friendly and robust firewall solution for Linux? Look no further than firewalld. With its command line and GUI interfaces, configuring this modern and powerful firewall has never been easier. This article is presented in partnership with Incogni, as part of Cybersecurity Awareness Week.
Why Do You Need a Firewall?
Network connections are established between an origin and a destination. The software located at the origin initiates the request for the connection, while the software at the destination has the authority to accept or reject it. In case of acceptance, network traffic, which refers to packets of data, can freely flow in both directions through the established connection. This applies whether you are sharing information within your own living space, remotely accessing your work from a home office, or utilizing a cloud-based resource located far away.
In order to enhance security, it is recommended to limit and control the connections to your computer. This can be achieved through the use of firewalls, which act as filters for network traffic based on criteria such as IP address, port, or protocol. By configuring firewall rules, you can determine which connections are allowed or denied. Think of firewalls as the security personnel at an exclusive event, only allowing entry to those on the approved list.
However, it is important to strike a balance with your firewall rules. You don't want them to be overly restrictive and hinder your normal activities. The key is to simplify the configuration process of your firewall, reducing the chances of unintentionally creating conflicting or overly strict rules. Many users express their reluctance to use a firewall due to perceived complexity or difficulty in understanding the command syntax.
Firewalld is a robust and user-friendly firewall solution that can be easily configured using either the command line or its dedicated GUI application. Linux firewalls utilize netfilter, the network filtering framework built into the kernel. In user-land, there are several tools available to interact with netfilter, including iptables, ufw (the uncomplicated firewall), and firewalld. However, we believe that firewalld provides the optimal combination of features, precision, and ease of use.
Installing firewalld
Firewalld consists of two components: the firewall functionality provided by the daemon process and the optional GUI called firewall-config. It is important to note that firewall-config does not contain a "d" in its name.
Installing firewalld on Ubuntu, Fedora, and Manjaro is a straightforward process. However, it is important to note that each operating system has its own pre-installed components and bundled features.
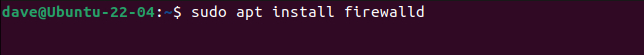
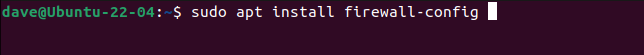
For Ubuntu, the installation requires the installation of firewalld and firewall-config packages.
sudo apt install firewalld
sudo apt install firewall-config
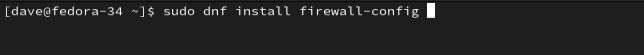
On Fedora, firewalld is already installed. We just need to add firewall-config .
sudo dnf install firewall-config
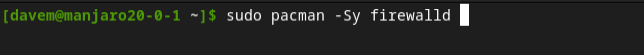
On Manjaro, neither component is pre-installed, but they're bundled into a single package so we can install them both with a single command.
sudo pacman -Sy firewalld
We need to enable the firewalld daemon to permit it to run each time the computer boots up.
sudo systemctl enable firewalld
And we need to start the daemon so that it is running now.
sudo systemctl start firewalld
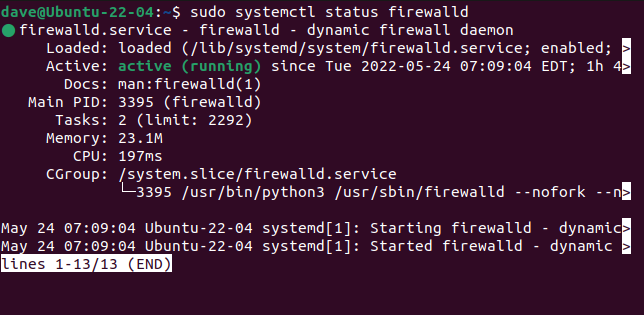
We can use systemctl to check that firewalld has started and is running without issues:
sudo systemctl status firewalld
We can also use firewalld to check whether it is running. This uses the firewall-cmd command with the --state option. Note there's no "d" in firewall-cmd :
sudo firewall-cmd --state
Now we've got the firewall installed and running, we can move on to configuring it.
The Concept of Zones
The firewalld firewall operates on a zone-based system. Zones consist of firewall rules and a corresponding network connection. This allows customization of zones with different security restrictions to suit specific requirements. For instance, there can be a zone designated for normal daily operations, another zone for enhanced security measures, and even a complete lockdown zone with no inbound or outbound connections.
To transition from one zone to another, and consequently switch security levels, simply reassign your network connection from its current zone to the desired zone.
Moving from one defined set of firewall rules to another is made extremely efficient. Another viable application of zones is to assign one zone to your laptop when you are at home and another when you are connected to public Wi-Fi.
firewalld provides nine pre-configured zones, which can be customized, as well as the option to include additional zones or remove existing ones.
Content
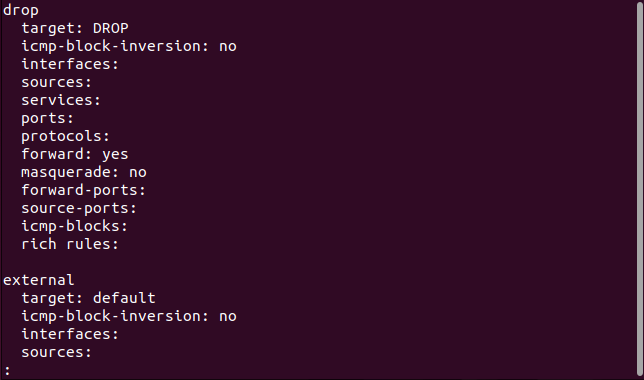
Drop: Any incoming packets will be discarded. However, outgoing traffic is permitted. This is considered the most cautious configuration.
Block: All incoming packets are discarded, and an icmp-host-prohibited message is sent back to the sender. Outgoing traffic is still allowed.
trusted: All network connections are accepted and other systems are considered trustworthy. This setting should only be used in highly secure environments such as captive test networks or your own home.
public: This zone is intended for public or other untrusted networks where none of the other computers can be relied upon. Only a limited number of commonly known and generally safe connection requests are approved.
external: This zone is meant for utilization on external networks where NAT masquerading (port forwarding) is enabled. Your firewall functions as a router, directing traffic to your private network, which remains accessible but remains private.
internal: This zone is designed for usage on internal networks wherein your system operates as a gateway or router. Other systems on this network are typically considered trustworthy.
dmz: The "demilitarized zone" (DMZ) is designated for computers located outside of your main network defenses, with restricted access back to your network.
work: This zone is exclusively intended for work machines. Other computers within this network are typically considered reliable.
Home: This zone is designated for machines used within the home. Typically, other computers on this network are considered trustworthy.
While the home, work, and internal zones serve similar purposes, dividing them into separate zones enables the customization of each zone according to specific preferences. This enables the encapsulation of distinct rules for individual scenarios.
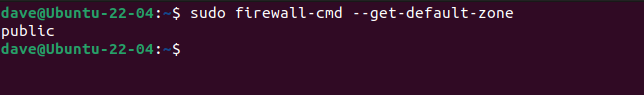
A good starting point is to find out what the default zone is. This is the zone that your network interfaces are added to when firewalld is installed.
sudo firewall-cmd --get-default-zone
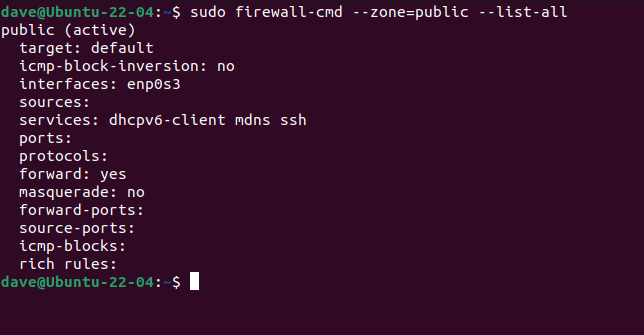
Our default zone is the public zone. To see the configuration details of a zone, use the --list-all option. This lists anything that has been added or enabled for a zone.
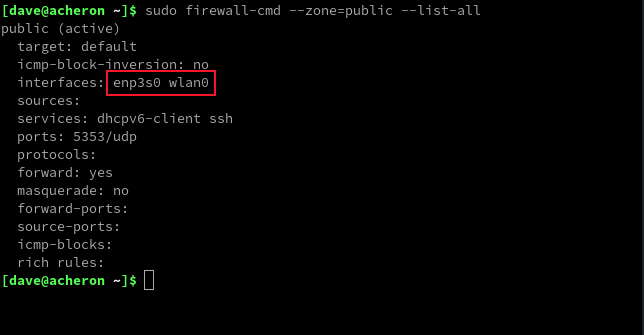
sudo firewall-cmd --zone=public --list-all
The association of this zone with network connection enp0s3 allows for the traffic related to DHCP, mDNS, and SSH to pass through. The activation of this zone is indicated by the addition of at least one interface.
firewalld provides the capability to include desired services in a zone to permit traffic from them. By doing so, the respective type of traffic is automatically allowed through. This simplifies the process of configuring specific details such as the port number (5353) and protocol (UDP) for mDNS. Of course, manual configuration of these details is also possible.
If we run the previous command on a laptop with an ethernet connection and a Wi-Fi card, we'll see something similar, but with two interfaces.
sudo firewall-cmd --zone=public --list-all
We have included both of our network interfaces in the default zone. The zone now includes rules for the same three services as the previous example, with the addition of DHCP and SSH as individually identified services. Additionally, mDNS has been included as a port and protocol combination.
To list all zones use the --get-zones option.
sudo firewall-cmd --get-zones
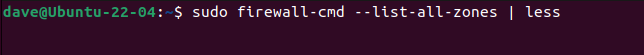
To see the configuration for all zones at once, use the --list-all-zones option. You'll want to pipe this into less.
sudo firewall-cmd --list-all-zones | less
This is useful because you can scroll through the listing, or use the search facility to look for port numbers, protocols, and services.
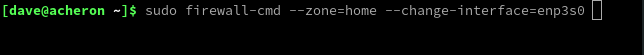
We can easily switch our Ethernet connection from the public zone to the home zone on our laptop using the --zone and --change-interface options.
To do this, execute the following command:
sudo firewall-cmd --zone=home --change-interface=enp3s0
Let's take a look at the home zone, and see if our change has been made.
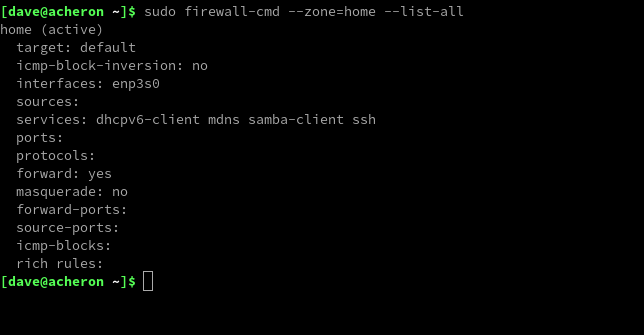
sudo firewall-cmd --zone=home --list-all
And so it happens. Our Ethernet connection is now integrated into the home zone.
Nevertheless, this alteration is only temporary. The modification we made affects the live configuration of the firewall, rather than its saved configuration. Should we restart or opt for the --reload option, our previous settings will be restored.
To ensure a lasting modification, the --permanent option must be utilized. This enables us to modify the firewall temporarily for specific needs without affecting the saved firewall configuration. Additionally, it allows us to examine and verify alterations before applying them to the configuration. When aiming to make our modification permanent, we should adhere to the following format:
sudo firewall-cmd --zone=home --change-interface=enp3s0 --permanent
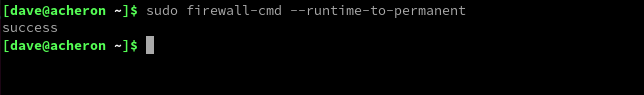
In case you make alterations without applying "--permanent" to all of them, you can save the configuration settings from the current firewall session to the configuration by utilizing the "--runtime-to-permanent" option.
sudo firewall-cmd --runtime-to-permanent
Adding and Removing Services
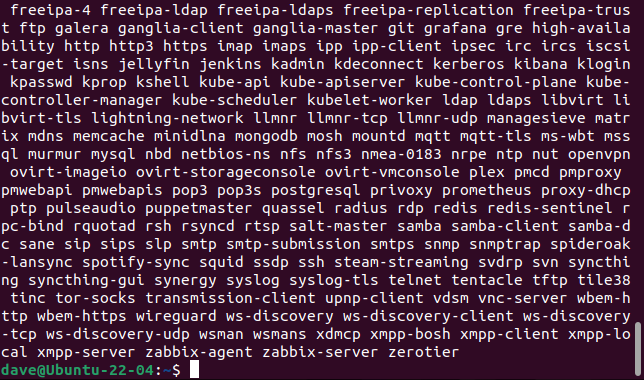
firewalld knows about a lot of services. You can list them using the --get-services option.
sudo firewall-cmd --get-services
Our version of firewalld listed 192 services. To enable a service in a zone, use the --add-serviceoption.
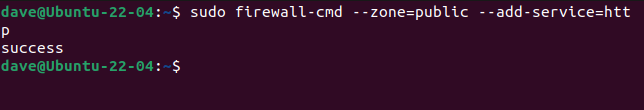
We can add a service to a zone using the --add-service option.
sudo firewall-cmd --zone=public --add-service=http
The name of the service must match its entry in the list of services from firewalld.
To remove a service replace --add-service with --remove-service
Adding and Removing Ports and Protocols
If you want to select the specific ports and protocols to include, you have the option to do so. You will need the port number and the protocol for the particular traffic you wish to add.
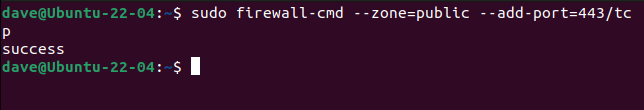
To include HTTPS traffic in the public zone, we can assign port 443, which corresponds to TCP traffic.
sudo firewall-cmd --zone=public --add-port=443/tcp
You could supply a range of ports by providing the first and last ports with a hyphen "-" between them, like "400-450."
To remove a port replace --add-port with --remove-port .
Using the GUI
Press your "Super" key and start to type "firewall." You'll see the brick wall icon for the firewall-config application.
Click that icon to launch the application.
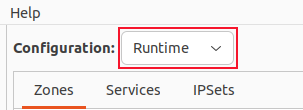
Adding a service to firewalld through the GUI is simple. You just need to select a zone from the available options and choose the desired service from the list. Additionally, you have the flexibility to modify either the running session or the permanent configuration by selecting either "Runtime" or "Permanent" from the "Configuration" dropdown menu.
To make modifications to the ongoing session and ensure the changes are effective after testing, select the "Runtime" option from the "Configuration" menu. Implement the desired alterations and, upon satisfaction with their functionality, employ the Options > Runtime to Permanent menu command.
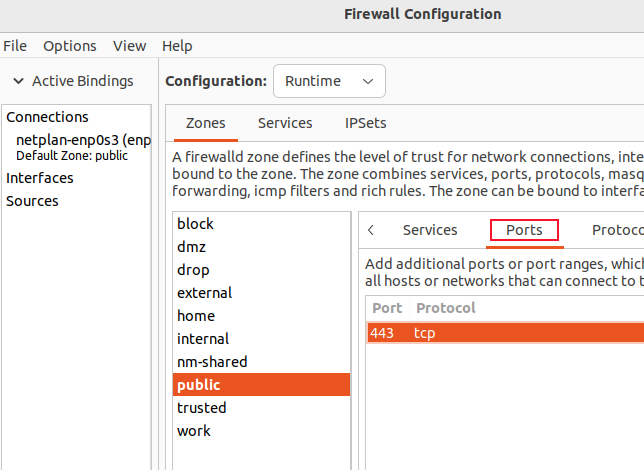
To enhance a zone with a port and protocol entry, simply choose the desired zone from the zone list and access the "Ports" section. By clicking on the add button, you can supply the port number and select the protocol from a dropdown menu.
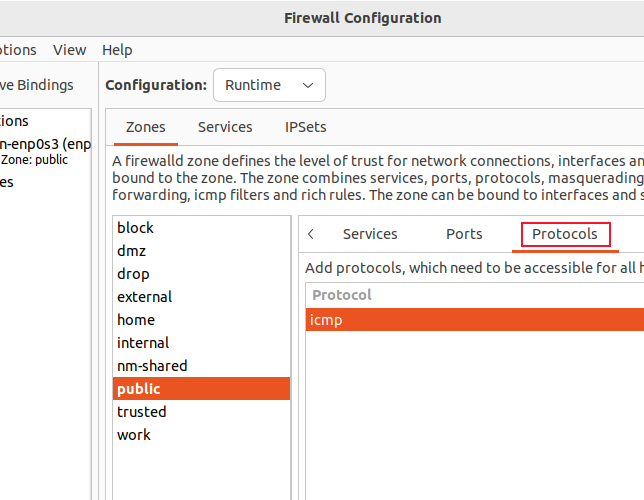
To add a protocol, click on "Protocols", click the "Add" button, and select the protocol from the pop-up menu.
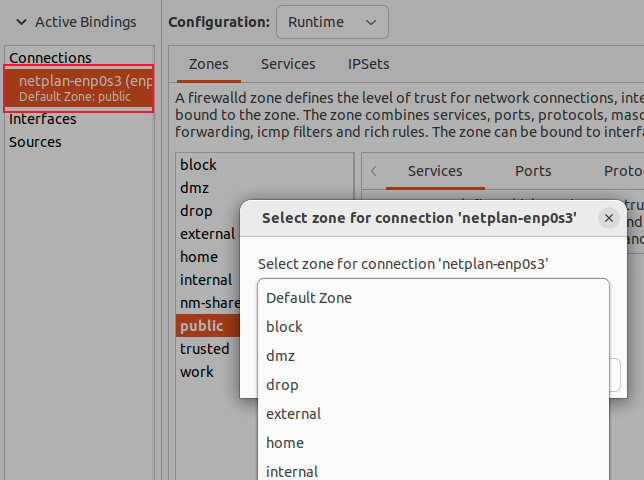
To move an interface from one zone to another, double-click the interface in the "Connections" list, then select the zone from the pop-up menu.
The Tip of the Iceberg
Firewalld can offer you countless possibilities, but the provided information will suffice to initiate and execute your desired tasks. By utilizing the knowledge given, you will have the capability to establish purposeful regulations within your zones.