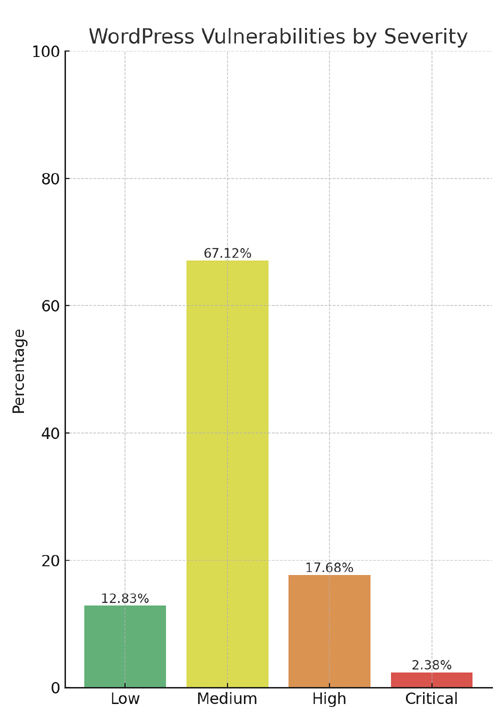2024 WordPress Security Study Reveals Common Mistakes Plaguing Websites

Discover the key findings from the 2024 WordPress security report highlighting errors that continue to jeopardize website security and lead to potential compromises. Learn how to safeguard your site against vulnerabilities and enhance its protection.
The 2024 WordPress vulnerability report from WPScan highlights important trends in WordPress security and provides insights for website publishers and SEOs to consider.
One key finding is that approximately 20% of vulnerabilities were classified as high or critical level threats, while the majority, at 67%, were medium severity threats. It is important to note that medium level vulnerabilities should not be underestimated as low-level threats, and they should be taken seriously and given proper attention.
The report does not blame users for the malware and website vulnerabilities. But mistakes made by publishers can amplify the success of hackers exploiting vulnerabilities.
The WPScan report advised:
WordPress Vulnerability Severity Distribution
Severity may not always indicate the likelihood of exploitation, but it serves as a valuable tool for website owners to determine when they should disable or update an extension.
Good news for WordPress publishers - critical level vulnerabilities, the highest threat level, make up only 2.38% of all vulnerabilities. However, when combined with high level threats (17.68%), the total number of concerning vulnerabilities rises to almost 20%.
Here are the severity ratings by percentages:
Critical 2.38%
Low 12.83%
High 17.68%
Medium 67.12%
Graph of WordPress vulnerabilities showing percentages by severity
Authenticated Versus Unauthenticated
Authenticated vulnerabilities are those that need an attacker to have user credentials and permission levels to exploit a vulnerability. Exploits needing subscriber-level authentication are the most exploitable, while those needing administrator access pose less risk, although not always low risk for various reasons.
Unauthenticated attacks are usually the easiest to exploit since anyone can launch an attack without needing a user credential.
Nulled Software And Weak Passwords
The WPScan vulnerability report revealed that approximately 22% of reported vulnerabilities did not require any authentication or only needed subscriber level access, making them the most easily exploitable vulnerabilities. On the other hand, vulnerabilities that required admin permission levels accounted for 30.71% of the reported vulnerabilities.
Weak passwords and nulled plugins are often the culprits behind malware detected by the Jetpack Scan. Nulled plugins are pirated software that have had their validation ability disabled, making it easier for them to be infected with malware. These plugins often have backdoors that allow for malicious attacks. Additionally, weak passwords are vulnerable to brute-force attacks.
According to the WPScan report:
Permission Levels Required For Exploits
Authentication bypass attacks can occur through various methods. These include taking advantage of weak passwords, attempting to guess login credentials, using brute force attacks to crack passwords, employing social engineering tactics like phishing or pretexting, utilizing privilege escalation techniques by exploiting known vulnerabilities in software and hardware devices, or trying default account logins.
The highest percentage of exploits are vulnerabilities that require administrator level credentials. Following this, Cross Site Request Forgery (CSRF) accounts for 24.74% of vulnerabilities. CSRF is an attack that tricks a user into unknowingly granting permission to a hacker by clicking on a malicious link. This is a common mistake that WordPress users should be cautious of, as it only takes one admin level user to fall victim to this attack, allowing the hacker to gain admin privileges on the WordPress website.
The percentages of exploits are categorized by the roles needed to carry out an attack.
Ascending Order Of User Roles For Vulnerabilities
Author 2.19%
Subscriber 10.4%
Unauthenticated 12.35%
Contributor 19.62%
CSRF 24.74%
Admin 30.71%
Most Common Vulnerability Types Requiring Minimal Authentication
Broken Access Control in WordPress is when a security loophole allows unauthorized users to access higher levels of permissions without the necessary credentials.
When examining unauthenticated or subscriber level vulnerabilities in the report, WPScan shows the percentages of common vulnerability types that are easy to exploit due to minimal or no user authentication required.
According to the WPScan threat report, Broken Access Control is the most common threat at 84.99%, with SQL injection following at 20.64%.
Broken Access Control, as defined by the Open Worldwide Application Security Project (OWASP), is:
Access control, also known as authorization, determines which users can access specific content and functions on a web application. This process occurs after authentication and dictates the actions that authorized users can take.
Implementing access control may seem straightforward, but it can be challenging to get it right. The access control model of a web application is intricately linked to the site's content and features. Furthermore, users may belong to various groups or roles with different levels of abilities and privileges.
SQL injection is the second most common vulnerability, accounting for 20.64% of all vulnerabilities. WPScan has categorized it as a high severity and risk issue. This type of vulnerability is particularly dangerous because attackers can easily access and manipulate the database, which is crucial for every WordPress website.
Broken Access Control 84.99%
SQL Injection 20.64%
Cross-Site Scripting 9.4%
Unauthenticated Arbitrary File Upload 5.28%
Sensitive Data Disclosure 4.59%
Insecure Direct Object Reference (IDOR) 3.67%
Remote Code Execution 2.52%
Other 14.45%
Vulnerabilities In The WordPress Core Itself
In 2023, there were a total of 13 vulnerabilities reported in the WordPress core itself. Most vulnerability issues are usually found in third-party plugins and themes. Out of these thirteen vulnerabilities, only one was considered a high severity threat. The severity rating system is maintained by the Common Vulnerability Scoring System (CVSS), with Critical being the highest level threat.
Website Security Should Be Prioritized for Technical SEO
The WordPress core platform is maintained at the highest standards and is supported by a global community that works diligently to identify and fix any security vulnerabilities.
Site audits usually do not include website security, but I believe that every thorough audit should address security headers. I have always emphasized the importance of website security because once a website's ranking starts dropping from the search engine results pages (SERPs) due to a vulnerability, it becomes an SEO issue. That's why it is crucial to take proactive measures to ensure website security.
Based on the WPScan report, leaked credentials and weak passwords were identified as the main points of entry for hacked websites. Implementing strong password standards and utilizing two-factor authentication are essential components of enhancing a website's security measures.
Another effective way to enhance website security is by implementing security headers. These headers can help prevent Cross-Site Scripting and other vulnerabilities.
In addition, utilizing a WordPress firewall and implementing website hardening measures are proactive steps to boost security. I experienced firsthand the importance of this when I added a forum to a new website and it was targeted by attacks within minutes. It's surprising to know that almost every website globally is constantly under threat from bots searching for weaknesses.
Read the WPScan Report:
WPScan 2024 Website Threat Report
Featured Image by Shutterstock/Ljupco Smokovski
Editor's P/S:
The WPScan 2024 WordPress Vulnerability Report paints a sobering picture of the security landscape facing WordPress websites. While critical level vulnerabilities remain relatively low, medium severity threats account for a significant majority and should not be overlooked. The report emphasizes that user errors, such as weak passwords and nulled plugins, often provide an entry point for malicious actors.
The report also highlights the importance of implementing strong authentication measures, such as two-factor authentication, and employing security headers to prevent cross-site scripting and other vulnerabilities. It is concerning to note that almost every website globally faces constant threats from bots searching for weaknesses. Therefore, website owners and SEOs must prioritize website security as an integral part of technical SEO to prevent ranking drops and maintain a secure online presence.