10 Foolproof Tips to Fortify Your Gmail and Google Account Security

Guard your Gmail and Google Account with expert tips Safeguard your sensitive information by starting with a Security Checkup and setting up strong passwords, 2-step verification, and enhanced safe browsing Monitor connected apps, devices, and notifications for added protection
Key Takeaways
Start with a Security Checkup- Use the built-in Security Checkup tool to review and confirm important information to ensure your account security.
Update Sign-in and Recovery Options: Verify your recovery phone number and email address, and examine the devices authorized for login access.
Manage Apps with Account Permissions: Assess and remove access for any apps or devices that you no longer utilize or cannot recall authorizing.
Consider this: Google likely has the lion's share of your personal data among all your online accounts. Just think about it - if you rely on Gmail for your email, Chrome for browsing the web, and Android as your mobile operating system, then you're essentially entrusting Google with near-ubiquitous access to your digital life. Now, let's delve into the topic of fortifying the security of your Google account. This article on Cybersecurity Awareness Week is presented by Incogni.
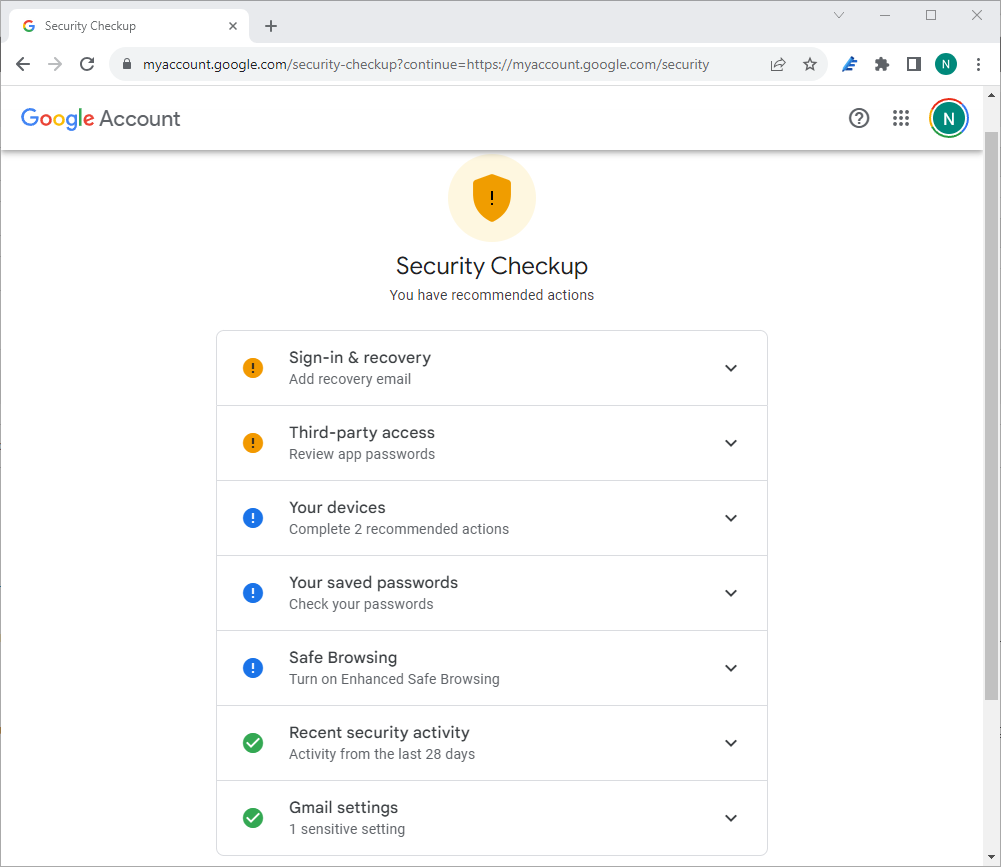
Start with a Security Checkup
Google makes checking your account security very easy: just use the built-in Security Checkup tool on your account's "Sign in & security" page.
When you select the "Protect Your Account" option, you will be directed to a multi-section form where you will be asked to carefully review and confirm certain information. It is advisable to allocate sufficient time and thoroughly examine the information provided here.
The sequence of these categories may vary according to Google's assessment of their importance. Your order may differ from ours, but the content of the categories remains unchanged.
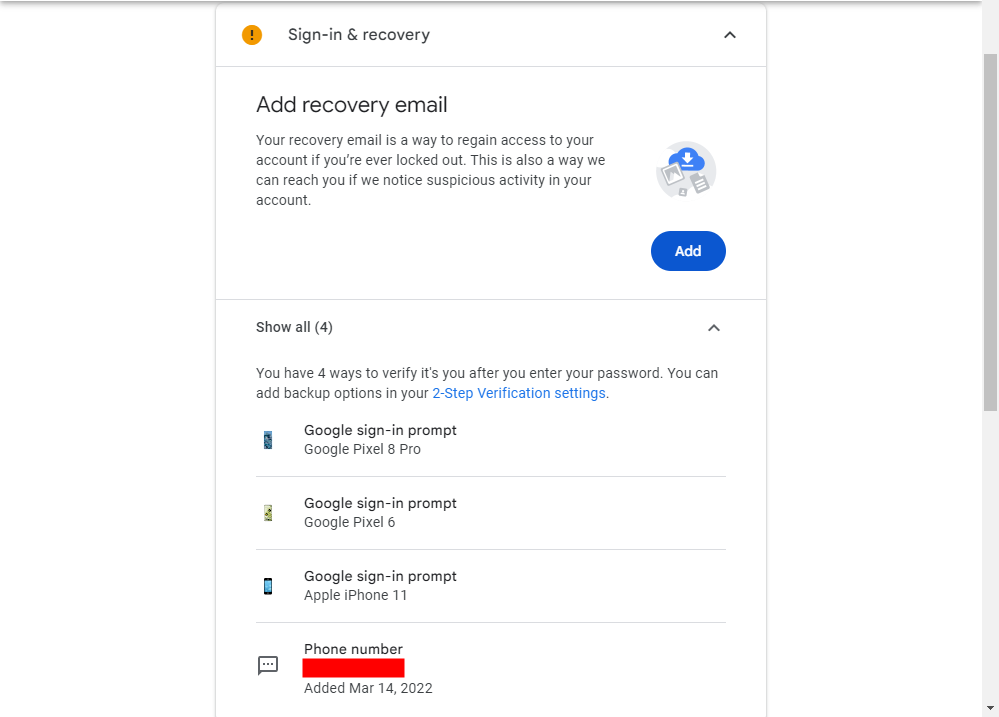
Set Sign-in and Recovery Options
To ensure hassle-free access to your Google account, simply verify your recovery phone number and email address, as well as the authorized devices for login. It is essential to have this information accurately configured to prevent any lockouts. Moreover, whenever your primary account is accessed from a different location, you will receive an email notification on your recovery account.
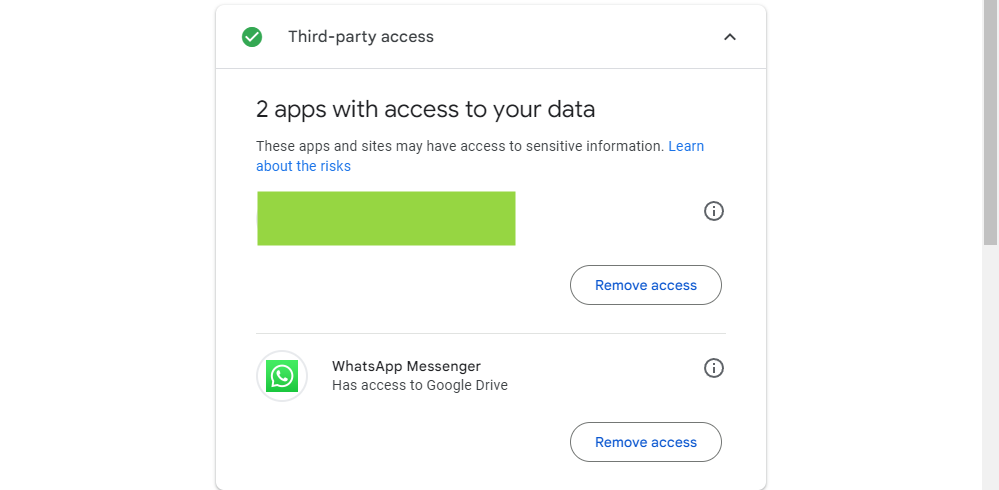
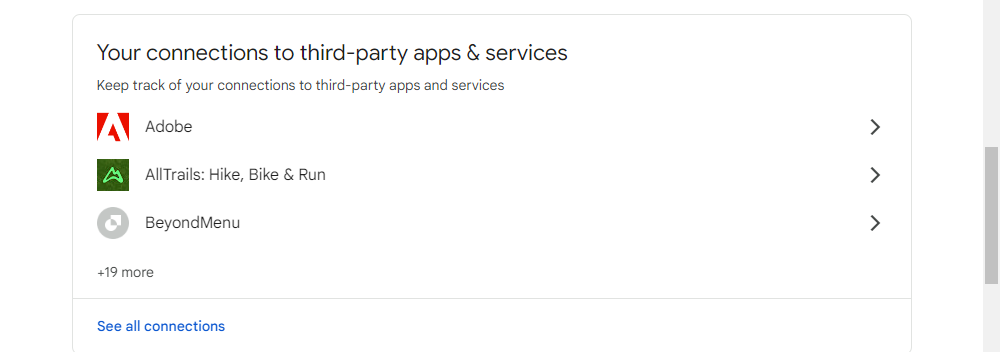
Clean Up Apps That Have Permission to Access Your Account
Next up is an essential section: Account Permissions. Essentially, this includes any entity that has authorization to your Google Account, such as apps or devices you have logged into using your Gmail credentials. The comprehensive list not only reveals the app or device, but also specifies the extent of its access. If you cannot recall granting access to a particular app or device (or if you no longer use it), simply click the "remove" button to withdraw its access to your account. In case you unintentionally remove an account you actually use, you will just need to reauthorize it the next time you log in.
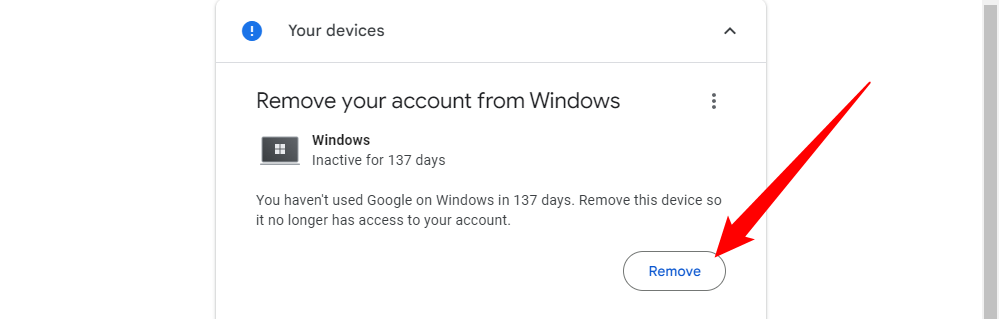
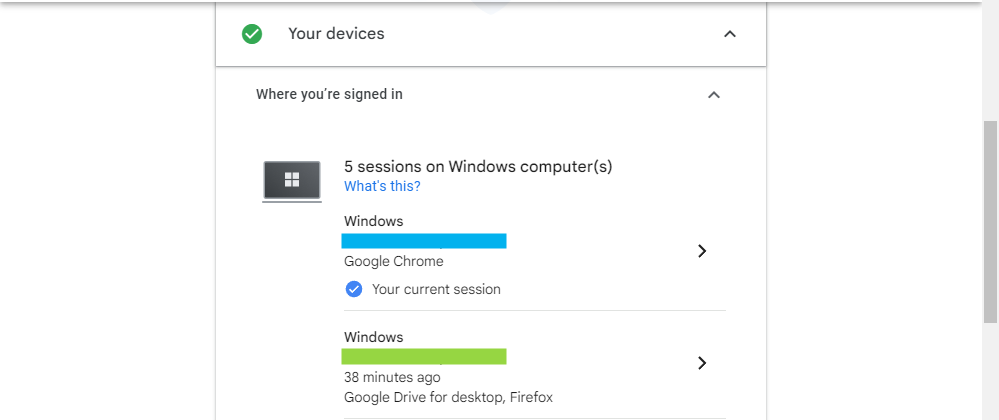
See What Other Devices Are Logged Into Your Account and Remove Old Devices
The following section's duration will vary depending on the number of devices connected. Pay attention to this section because if you no longer use a particular device, it should not have access to your account. It is important to know that the name of the device will be accompanied by the time, date, and location if you have recently used it. Google conveniently displays old devices that haven't been used to log in for a while at the top of the list. While this is not a highly critical security measure, it is still beneficial, especially if any of those devices have been lost or stolen.
To locate where you're signed in, scroll down slightly and click on the small arrow next to "Where You're Signed In." The information is categorized by operating system, allowing you to easily identify any suspicious access to your account. Keep in mind that if you utilize a VPN, the displayed locations may appear unfamiliar.
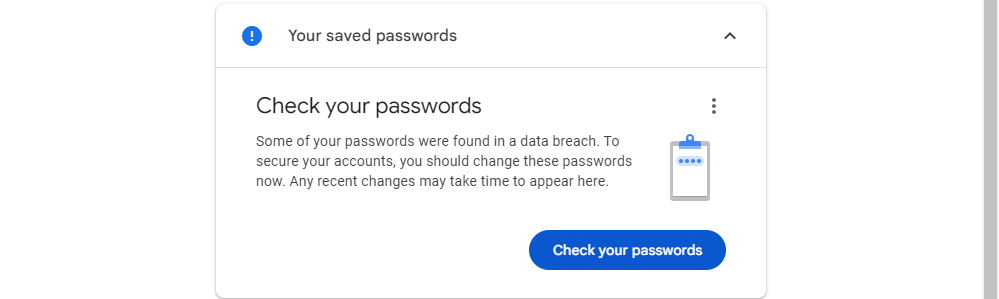
Change Compromised Passwords
If desired, you have the option to save passwords to your Google account. This prompt will appear frequently on Android devices and in Google Chrome. In the event that a password that has been saved to your Google Account is compromised, you will receive a notification indicating so.
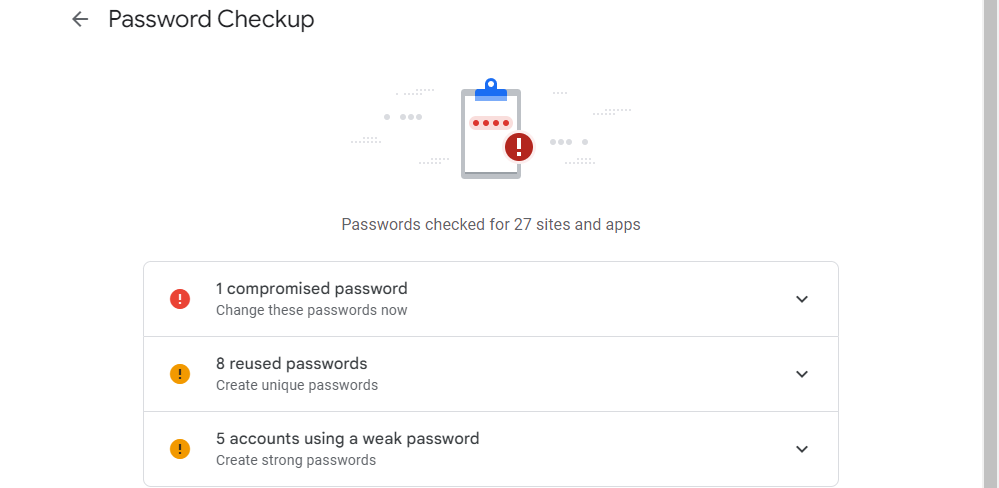
Before Google reveals any issues with your passwords, you must go through a series of verification processes. These measures encompass revealing compromised passwords, as well as identifying weak or reused passwords.
Credential stuffing poses a significant threat. It is crucial that you promptly change your compromised password and also update the password for any other account that shares a similar password. To illustrate, if your leaked password was "examplepassword1" for your Discord account, and you utilized "examplepassword2" as the password for your online banking login, it is imperative to modify both passwords accordingly.
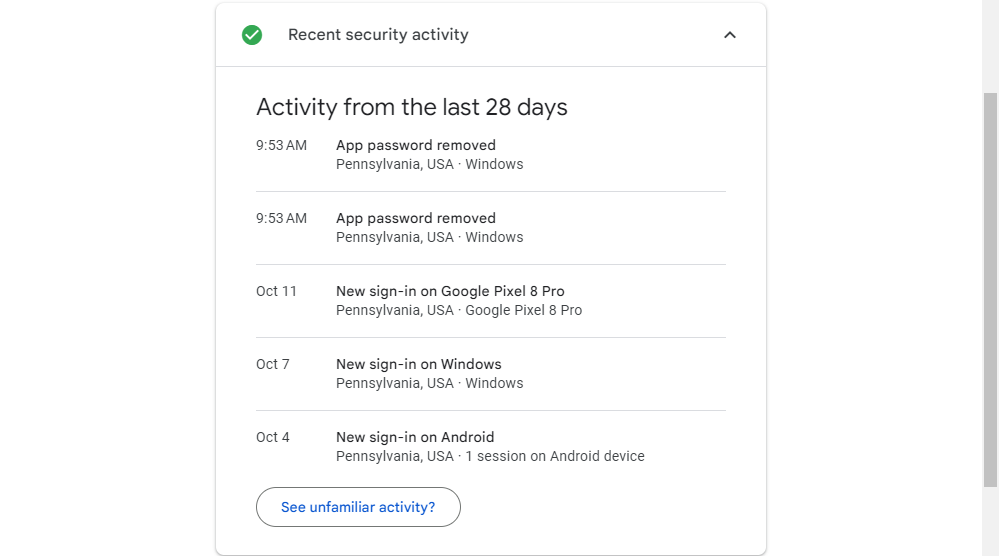
Check Recent Security Activity
The Recent Security Activity menu offers a user-friendly summary of all security-related alterations made on your account. Whether you create or delete a password, login from an unfamiliar location or using a new device, you will find a record of it here. If you come across any unexpected activity that you did not initiate, it is advisable to inspect it closely as it might signal suspicious behavior on your account.
If something does look amiss, click the "See Unfamiliar Activity" button to change your password and sign out of all devices in one click.
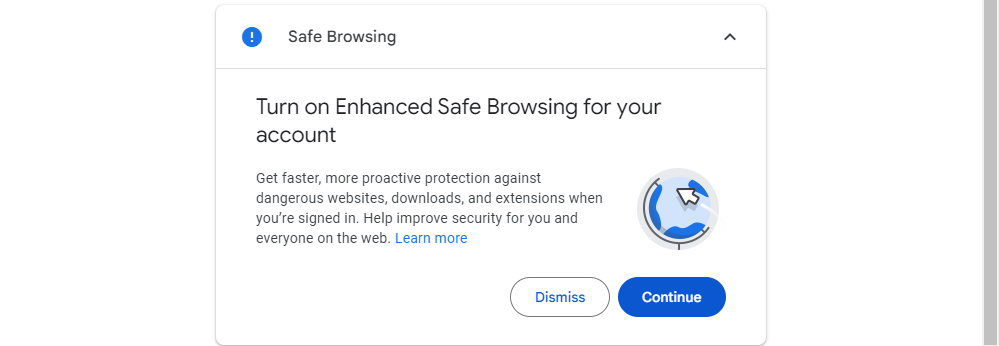
Enable Enhanced Safe Browsing (Optional)
Google provides additional browsing security features for your account, ensuring that your browsing experience remains safe. By filtering your search results in advance, Google actively prevents access to malicious websites. While not mandatory, you have the option to enable this feature if desired.
Use a Strong Password and 2-Step Verification
If you have spent a considerable amount of time on the internet, you are likely aware of the advice: create a strong password. Weak passwords, such as your child's name or birthday, your own birthday, or anything easily guessable, do not qualify as strong passwords. These types of passwords increase the risk of your data being stolen. It may be a harsh reality, but it is the truth.
We highly recommend using a password generator and manager to ensure the strongest passwords possible. It is even better if the manager is part of a password vault. Choose a reputable company for your password manager of choice.
Once you have a strong password, it is essential to set up 2-step authentication, also known as two-factor authentication (2FA). This means you need two components to access your account: your password and a second form of authentication that is only available to you. This can include receiving a unique code via text message, using an authentication app like Google Authenticator or Authy, or utilizing Google's codeless authentication system, which is our personal favorite.
By securing your device with both a password and physical possession, accessing your account becomes nearly impossible for anyone who only knows your password. They would also need to have stolen your phone in order to gain entry.
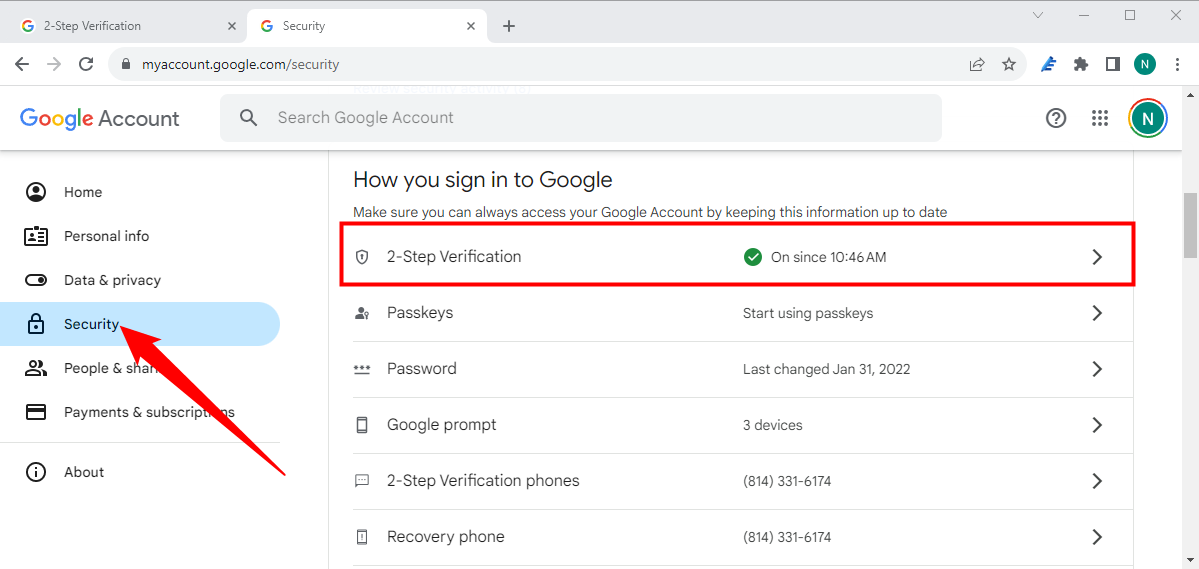
To change your password or enable two-step verification, begin by navigating to the Google Account Security Page. Then, scroll down to the "How You Sign In To Google" section where you will find relevant information such as the last password change and two-step verification setup date. To adjust or establish two-factor authentication, simply click on "2 Step Verification."
To change your password, click the "Password" box. You'll first be asked to input your current password, then be presented with a new password entry box. Easy enough.
Once you have set up 2-step verification (or if you already had it set up), you can customize your second step. This is where you have the option to switch to the convenient "Google Prompt" method without codes, switch to using an authenticator app, and ensure that your backup codes are up to date.
To set up a new second step method, just use the "Set up alternative second step" section.
Boom, you're done: your account is now much safer. Good for you!
Keep an Eye on Connected Apps, Device Activity, and Notifications
The remaining portion of the security page is quite straightforward (also included in the previously mentioned Security Checkup), as it deals with connected devices, applications, and notification preferences. Rather than requiring any active participation from your end, monitoring everything under "Device activity & notifications" and "Connected apps & sites" should be done passively.
Here you can keep track of your Google account's recent sign-ins, including the devices used. You can also view the currently logged-in devices and the apps that have access to your account.
Securing your Google account is a simple and time-effective process that is essential for all Google account holders. Google has done a remarkable job of ensuring convenience by consolidating all the necessary features in one user-friendly platform for easy access, management, and customization.